Release notes

- Version: 4.6.0
- Build number: 11919
- Release date: 2023-12-27 (general availability)
- Server version: nanitor-4.6.0.12001-13904-master
- Agent version: nanitor-4.6.0.11919-13898-master
- Collector version: nanitor-4.6.0.11919-13898-master
Welcome to Nanitor v4.6.0! This release brings a host of new features, improvements, and bug fixes to enhance your cybersecurity threat management experience. From external attack surface discovery to advanced network inventory insights, v4.6.0 is designed to provide a more comprehensive and efficient security posture management.
Highlights
External asset discovery
Leveraging Shodan, users can now discover and analyze their external attack surfaces, including IPs, domains, and services. This feature identifies external assets that are related to a specific set of defined domains.
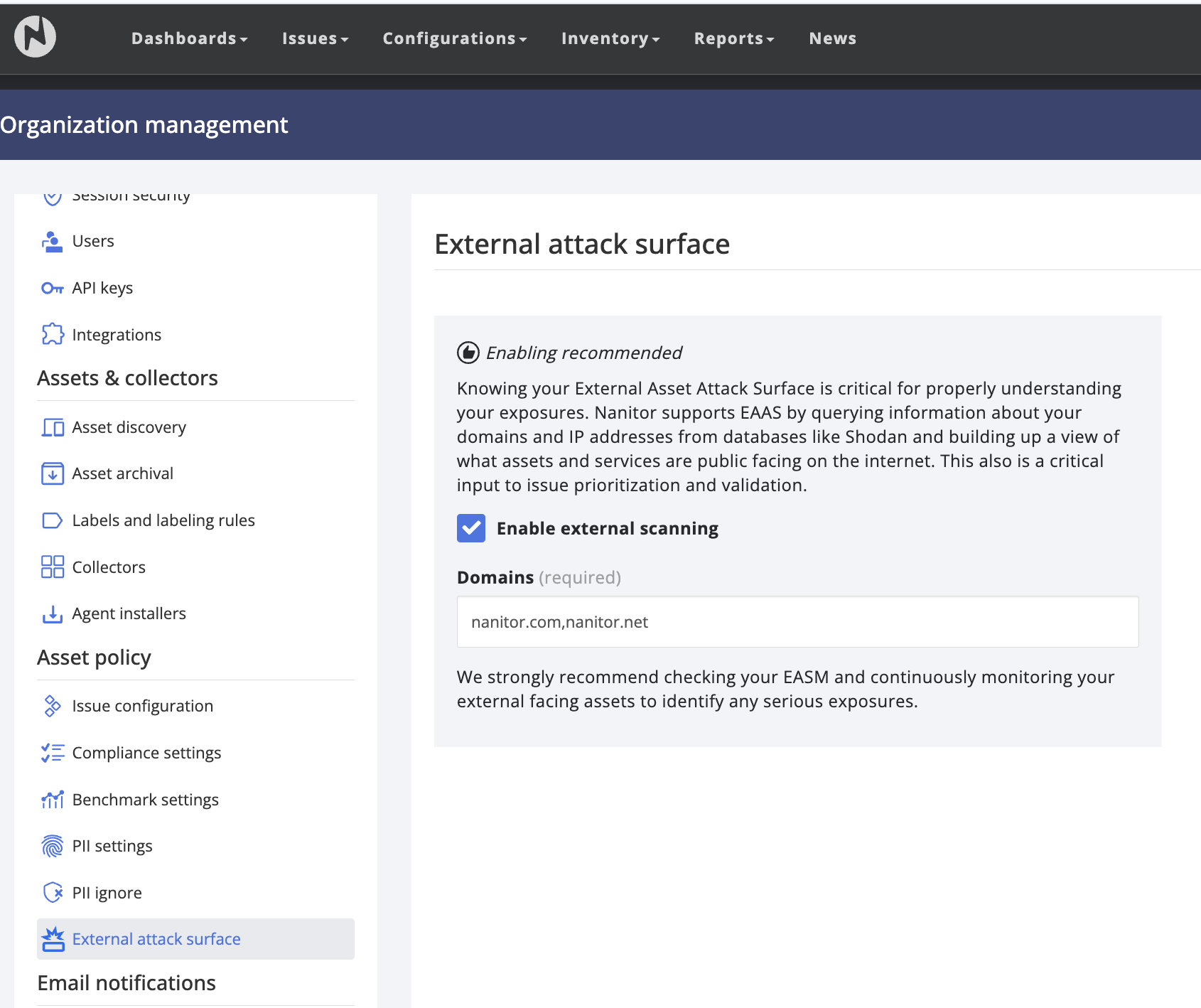
Users specify their owned domains under Organization management - Asset policy - External attack surface. The domains are specified as a comma separated list (if multiple).
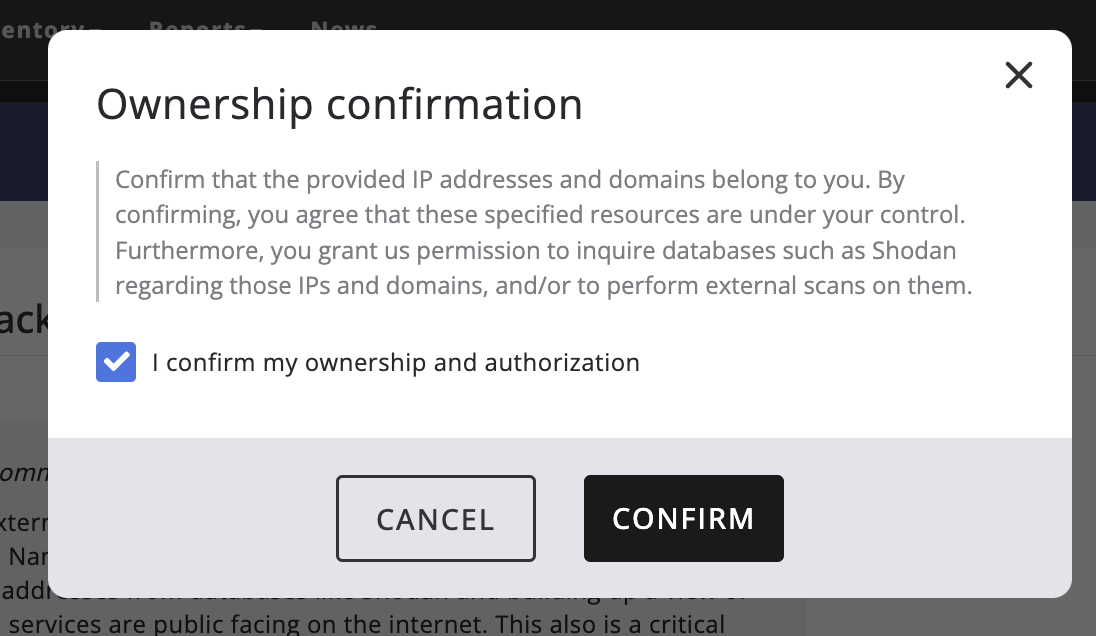
Users need to confirm their ownership of the domain and their authority to look up and view asset information from those domains.
Shortly after confirmation, external assets should start showing up under the Assets Inventory.
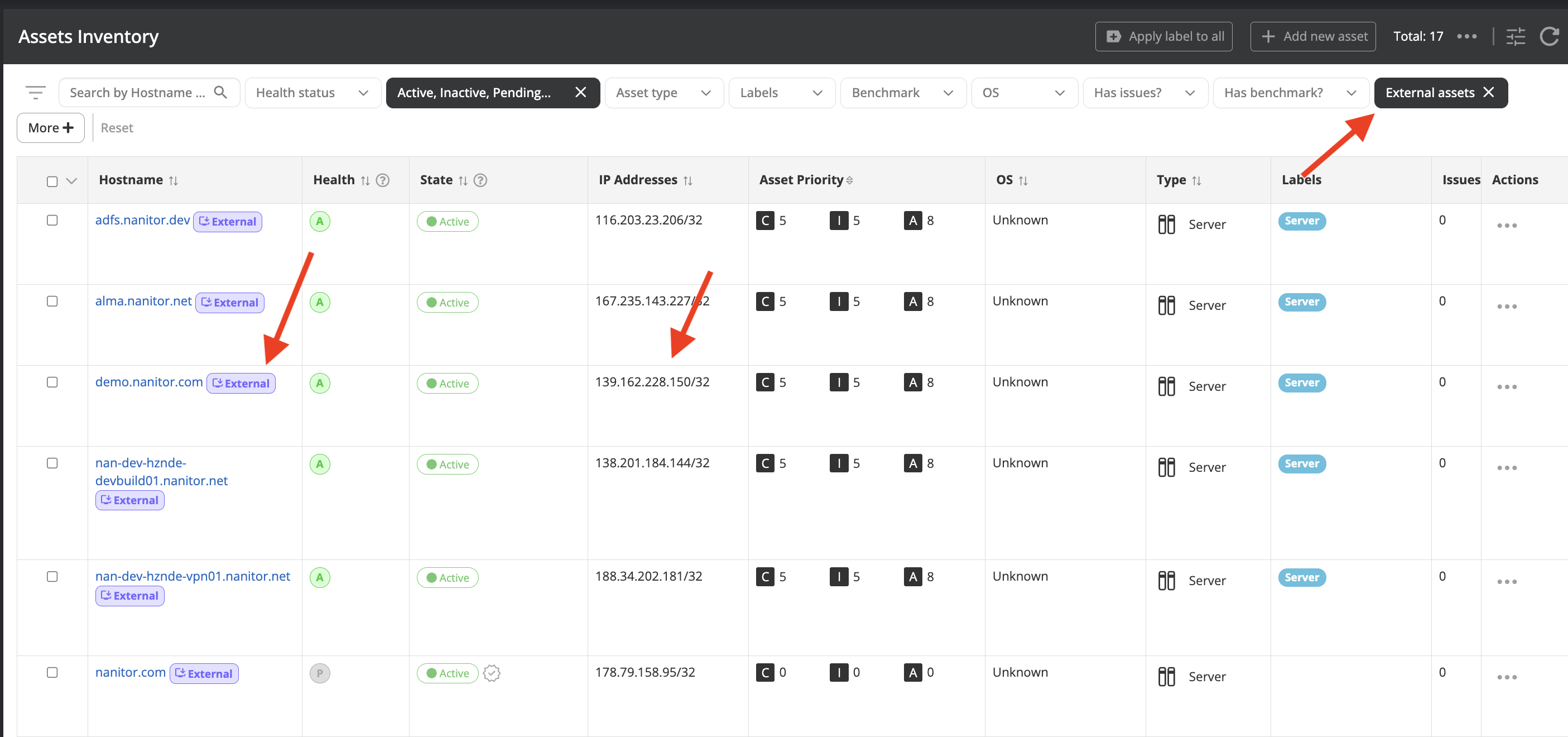
The check is repeated daily. Note that if assets are presistently detected for over 3 days then open ports will be shown in the Asset details to help identify services running and potential vulnerabilities.
We recommend going through the list of identified external assets and verifying that those should be available externally. Further, it can be helpful to verify that the assets are behind a web application firewall, and not directly exposed to the internet.
We are looking for feedback on this new feature. Please get in touch if there is anything more you would like to find out about your external assets.
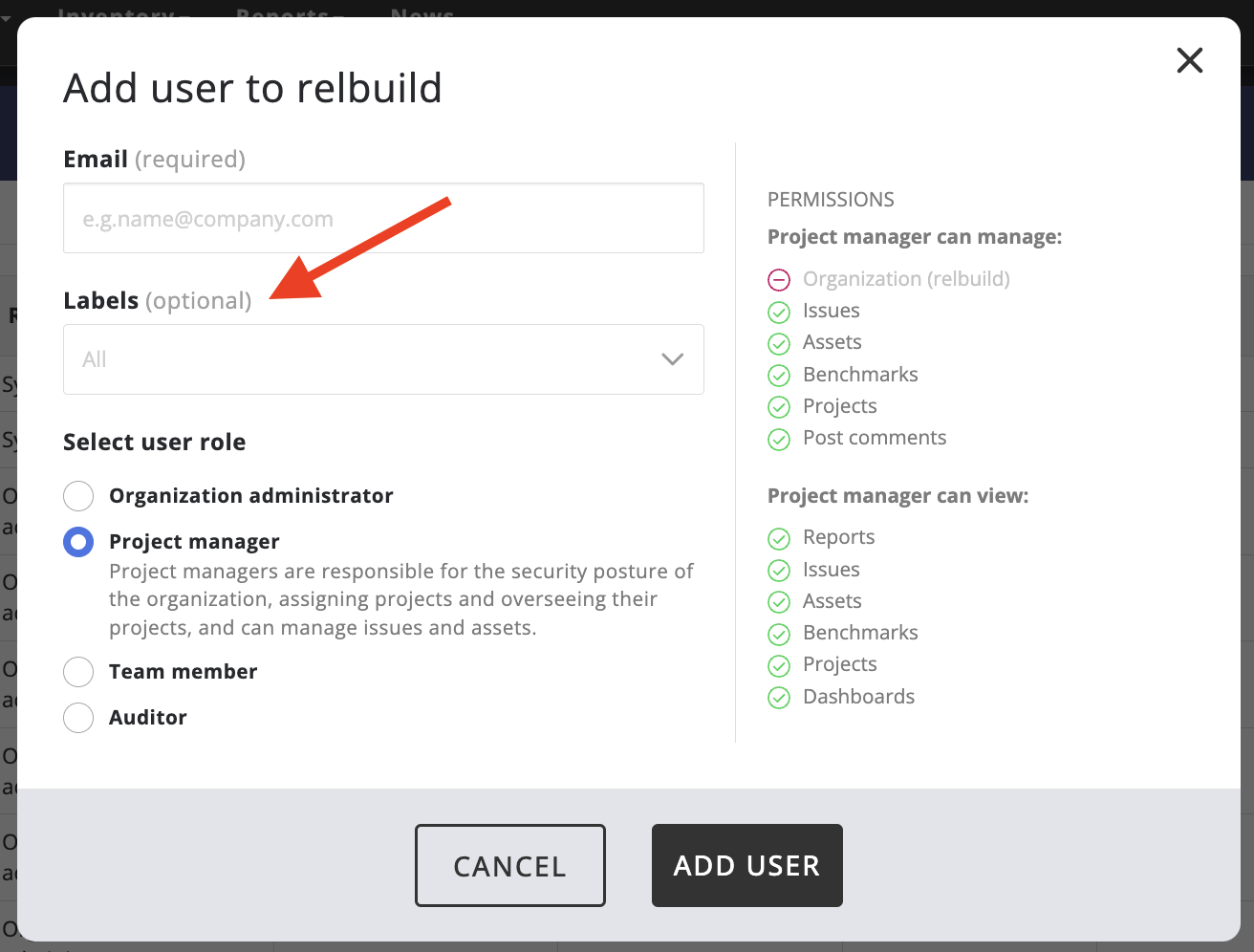
Asset-Label based scope restrictions
Enhance security management by assigning user access based on asset labels, allowing for more controlled and tailored access within the organization. Typically, it is recommended to give access only on a need-to-know basis, so limiting team members to a defined scope is a more secure practice.
The asset label scope restriction can be applied to users with project manager, team member or auditor roles within organizations.
Users with scope restrictions can generally only see information related to assets and issues that are within their scope. They are able to see some aggregated information such as Overview pages and other summaries, but are unable to drill further into the information.
We are very interested in feedback on this. Please get in touch if there is any aspect of this that is too limiting or does not work for your use case.
Network Inventory improvements
A new visual health indicator and asset priorities for networks provide clearer insights into network security health, aiding in asset discovery and network segregation.
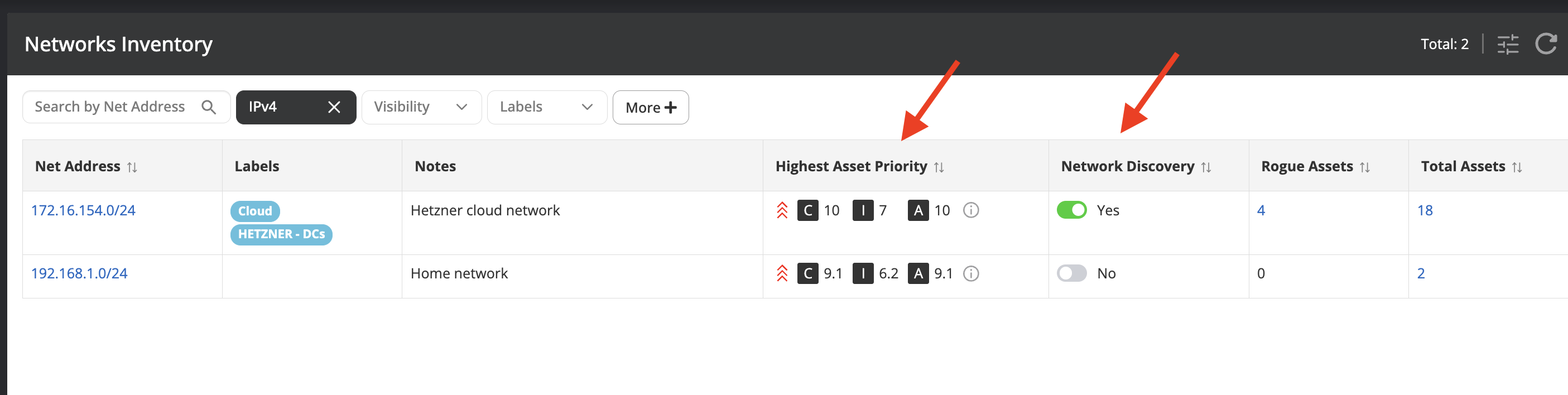
We recommend turning on Network Discovery on all critical networks, to ensure only monitored and authorized assets are on the critical networks.
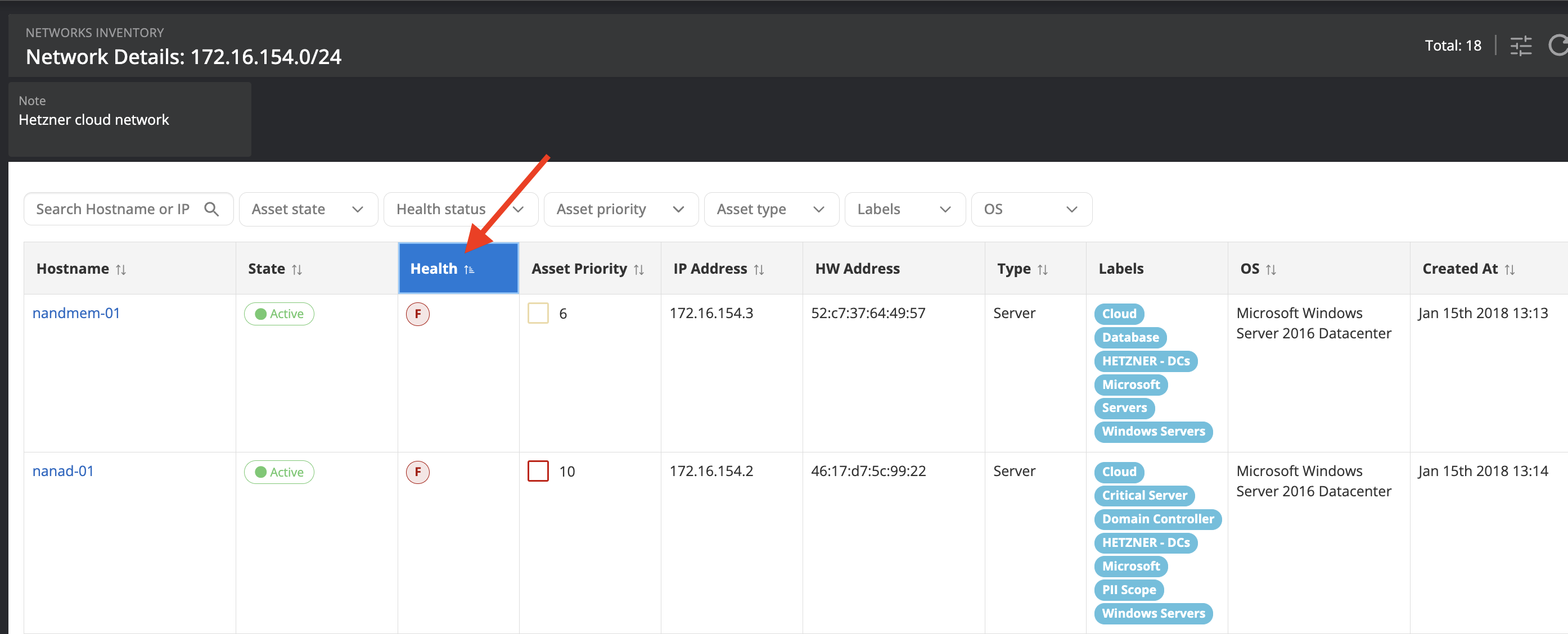
It is recommended to identify unhealthy assets on critical networks and harden them, or mitigate in other ways to reduce risk of lateral movement.
Network segregation security is an area that we believe is often overlooked. Therefore, we strongly recommend identifying, labeling and taking action on securing critical networks.
Saved filters
Users can now save and apply custom filters on selected pages for streamlined workflow and consistent analysis of defined metrics. This is initially being offered on the Asset Inventory and Issue List pages. The saved filters are saved per user. We are looking for feedback on this to help us decide whether to expand this to more pages.
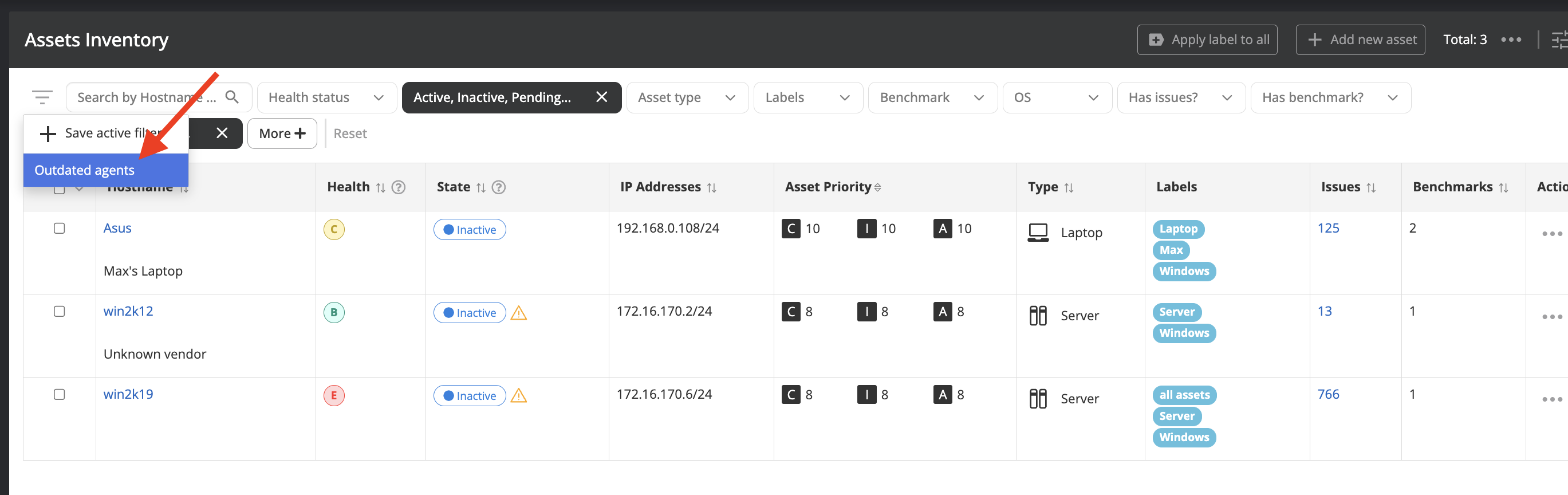
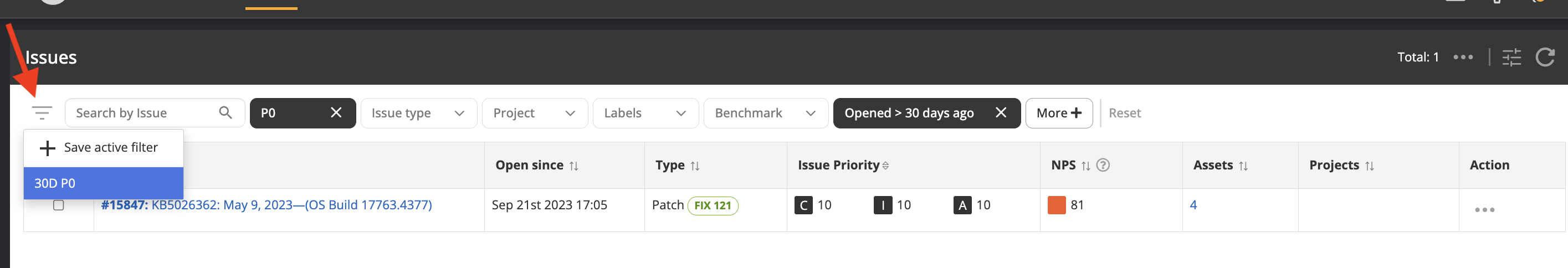
Improvements
- RBAC: Support converting existing users to system administrator role.
- Benchmark list: Added icon to highlight new/updated benchmarks.
- Benchmark details: Last updated timestamp added.
- Unassign a forced, manually assigned benchmark. Previously it was only possible to assign benchmarks to devices without any benchmark; now it is possible to reset it.
- Email content for scheduled reports has been cleaned up and improved.
- Detect CentOS 8 Stream correctly in system info. Improved detection to avoid confusion with Red Hat systems.
- Server resiliency: Make checkin more resilient to errors. In some cases asset checkins were not processed completely if an error came up. Updated to always try to update all the data, even in case of errors.
- Improved diagnostics: Capturing more server-side information to help troubleshoot bugs.
- Issue detail: A last checked timestamp has been added to the issue detail asset list tab.
- Issue detail: Forensics was improved for vulnerabilities/patches/misconfigurations to show only findings that are relevant, i.e. contributing to violation being flagged.
- Known vulnerabilities: Added ability to view CPE vectors for NVD supported vulnerabilities.
New Benchmarks
No new benchmarks were added in this release. More emphasis was put on testing and improving existing benchmarks.
Benchmark updates
The following benchmarks have been updated to the most recent version from CIS:
- F5 Benchmark (revision 9): based on CIS benchmark version 1.0.0 (F5 Networks Benchmark): Automated checks have been implemented for 32 rules.
- Cisco IOS 12 (revision 12): based on CIS benchmark version 4.0.0 (Cisco IOS 12 Benchmark): Multiple fixes made to failing rules following comprehensive testing.
- Cisco IOS 15 (revision 12): based on CIS benchmark version 4.1.1 (Cisco IOS 15 Benchmark): Multiple fixes made to failing rules following comprehensive testing.
- Cisco IOS 16 (revision 12): based on CIS benchmark version 2.0.0 (Cisco IOS 16 Benchmark): Multiple fixes made to failing rules following comprehensive testing.
- Cisco IOS 17 (revision 8): based on CIS benchmark version 2.0.0 (Cisco IOS 17.x Benchmark): Multiple fixes made to failing rules following comprehensive testing.
Bug Fixes
- Linux benchmark scripts: Check run from /tmp failing. Was causing multiple linux benchmark checks to work incorrectly.
- Collected asset shows ACTIVE but collection fails. Fixes made to ensure collected devices's last activity timestamp indicates when/if a successful connection was made.
- Resolution of discrepancies in the Overview dashboard vulnerability count.
- Correction of agent-up-to-date filter returning incorrect assets (Asset Inventory).
- Addressed issue with archived assets not returning to active state when the agent failed to start up due to Bitlocker.
- Cached data from a previous organization will no longer be retained when switching to a different organization.
- Active Directory Asset discovery: Exclude managed service accounts.
- Red Hat servers were not updating to the latest agent in some cases.
- Oracle 8.8 servers were incorrectly identified as Red Hat 8.8.
- Various fixes in asset management and user interfaces.
- Various fixes related to the recently added RBAC feature.
Helpful articles
How to perform manual upgrade on self-hosted servers
Updates
- 2023-12-19: Initial v4.6.0 release was published and released to early-access users.
- 2023-12-27: Release published for general availability.
- 2024-01-03: New build published (server only) to address a bug where the external asset discovery was not updating and the scheduled task was crashing on the server side: nanitor-4.6.0.12001-13904-master.