Health Status Dashboard
Nanitor Health Scores
The Nanitor Health Score system provides a simple way to understand the cybersecurity status of your overall organization including details down to individual assets in terms of compliance with the technical security policy as set in Nanitor.
The health score is calculated based on the unified issue system that Nanitor utilizes where each issue is a potential security problem and in violation of the technical security policy.
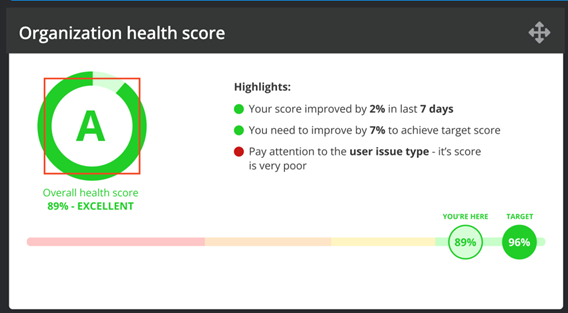
The Organization Health Score (OHS) gives a snapshot of the state of the organization. The OHS is built from the bottom up, where every single asset and its criticality is reflected in the score. Thus, it gives an important overview for management on how the organization is doing overall and breaks it down into fundamentals. The OHS enables managers to set measurable goals and drive decisions about where to invest and put efforts into improvements.
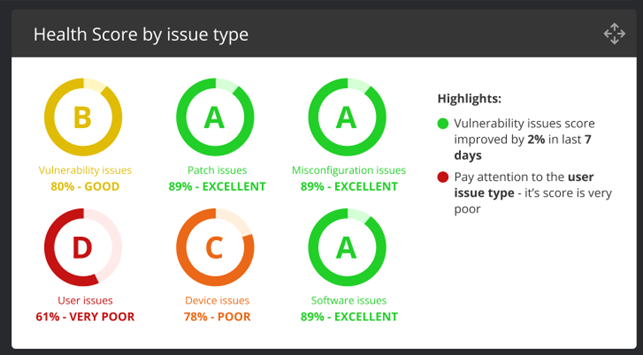
The health scores can also be broken down by issue type to get a good grasp of what fundamental areas most improvements are needed across the entire organization.
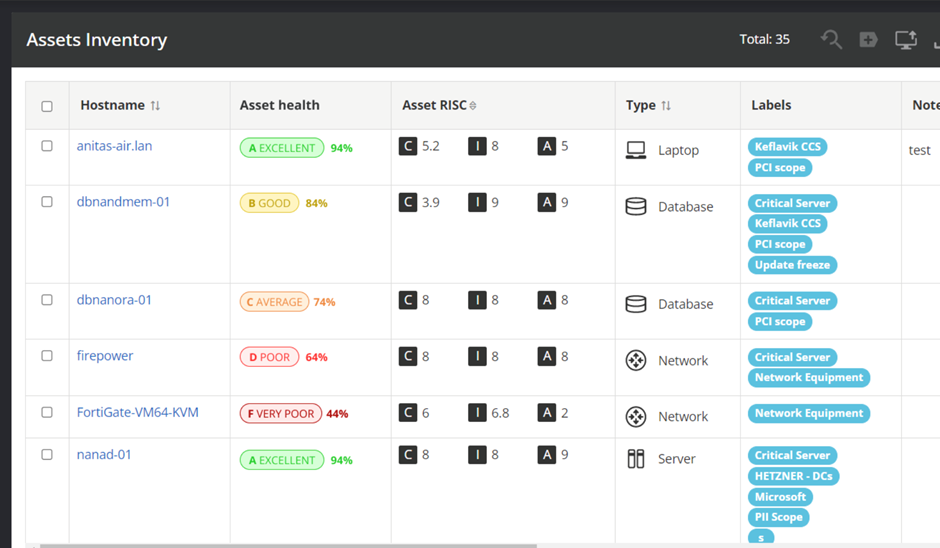
The Asset Health Score (AHS) reflects the state of each asset. Your device might be doing well in terms of security patches, but poorly in misconfigurations, in which case the score would reflect that status. Each key issue type is related to a fundamental area of cybersecurity: misconfiguration, vulnerabilities, patches, etc.
To be considered fully healthy, an asset needs to be doing well in each fundamental area. Similarly, there is a limit to how much each area can drag an asset down. Thus, each fundamental has a weight, and the asset gets a score of 0 - 100% in each area and then the asset score is calculated based on the weights of each fundamental area.
The fundamental score weights are indicative of both how important that area is to asset health, as well as how much coverage Nanitor has for the different fundamentals.
The Health Scores are composed of key cybersecurity fundamental controls and are in alignment with best practices and widely used compliance standards such as NIST and CIS controls:
1. Security configurations (30%) are a vital part of device security and poor configurations can lead to a system that is with too high trust, too many open services, and possibly even open holes and default accounts and passwords. Poor configurations lead to a high blast radius in case an attacker gets into one system. The security configuration fundamental counts for 30% of the final asset health score.
2. Known vulnerabilities (30%) can be considered equivalent to open holes that are easy to exploit, often with public exploits available that anyone can download. Remediation of known vulnerabilities is key to a healthy asset posture. The known vulnerabilities fundamental count for 30% of the final asset health score.
3. Security patches (20%) for critical vulnerabilities should be applied within a given period, typically 7 - 30 days depending on company policy. While related to known vulnerabilities, patching is measured separately, and is indicative of the performance of the patching teams, and days to patch is a KPI for the patching teams. Security patch issues count for 20% of the final asset health score. Note that for systems where security patches are not applicable, the security patches have no weight.
4. User issues (10%), including control of administrative privileges, are an important portion of security and this factor contributes to 10% of the final asset health score, where used. Note that if user issue checking is disabled then this component is not added to the health score.
5. Device issues (10%) are issues for a given device that do not fit into other categories. For example, end-of-life operating systems, unapproved open ports, etc. This category has a 10% weight. Note if no device issue checks are configured the weight goes down to 0.
6. PII issues (10%) are applicable where personally identifiable information such as credit cards and social security numbers should not be stored, and findings indicate issues that need to be addressed. The health score for PII ranges from 0 - 10%, 0% if not enabled, and can go up to 10% weight when enabled.
Note that those are baseline weights. The weights may vary depending on company industry size, risk appetite, and such. In addition, when features are not enabled, the other weights change dynamically and evenly such that the sum is always 100%.
The Health Scores provides a powerful cybersecurity management functionality, where the status can be viewed, target set, and progress clearly tracked towards milestones in a systematic fashion.
Available Health Score widgets
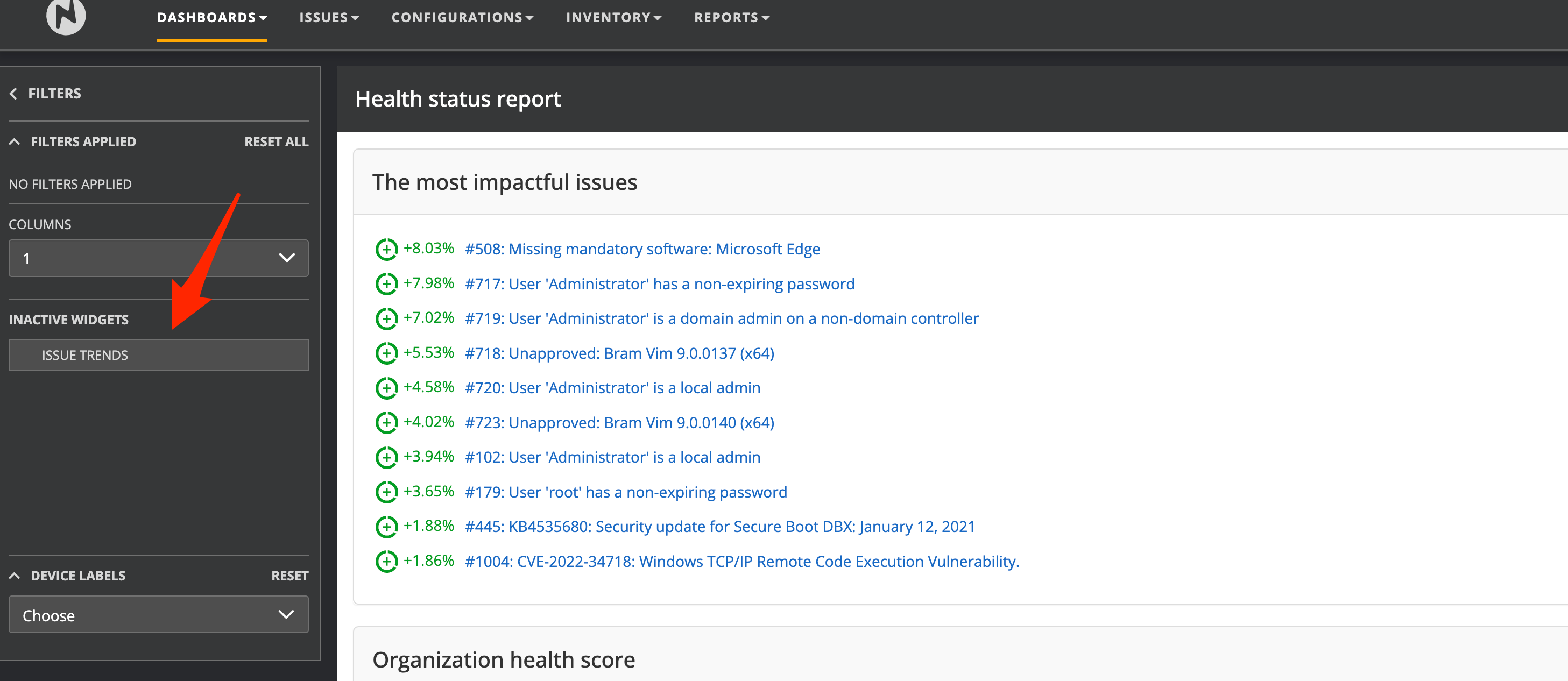
From the filter on the left-hand side, there are multiple widgets available that can be placed on the dashboard. Check this area for possible additional available widgets that can be placed on the health dashboard.
Inactive widgets can be placed on the dashboard by drag and drop.
FAQ
Can I compare my OHS with other companies?
This is possible, but keep in mind that the OHS is not an absolute measure and depends on how your technical security policies are configured.
An organization with a high maturity and a lot of controls requires more effort to reach a high score.
Can I get the formulas for the OHS?
We will be creating a whitepaper with a more precise specification of all the steps.
Will you ever update the formulas for health?
The goal is to support our customers to enforce a technical security policy. We may update the formulas and add more issue types, update weights, and such as we think is an improvement. Changes to the formula may change your health scores, but any changes will be noted in our solution release notes.
What should my health target score be?
The target health score is reflecting your technical policies (benchmark rule set) and your configurations. Configurations tell Nanitor what to raise an issue for and the severity of those. The Nanitor health score also reflects your asset priority score. The health score is an absolute figure according to your rule set and priority rating. As such your health score should in the end always be on a desired scale of around 95%. It will still take time though to reach that target and it might take up to 3 years for larger organizations to reach that goal depending on their efforts. It is good practice to start with a target score of 70% and raise it in increments to 90 or 95% over a period of 1-3 years depending on the resources you have available for remediation tasks.