Vulnerabilities
What is a Vulnerability
A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system and can only be removed by applying security patches or software updates. If you can not completely remove it, you can apply what is known as compensating control. That is you can compensate for the vulnerability by controlling who and how the device or software is accessed. For example, if there is a vulnerability in a piece of software that is exploited by tricking the user into opening a specially crafted document, the best solution is to update the software that is free of that vulnerability, if that isn't possible or feasible you can compensate for that by restricting the user's ability to open random files of that type and teach the user not to open random documents from unknown people.
Vulnerabilities are fed into Nanitor from the National Vulnerability Database (NVD) maintained by the National Institute of Standards and Technology (NIST) in the USA. Nanitor is scraping the vulnerability database on a daily basis and each night newly discovered vulnerabilities are fed into Nanitor. Nanitor pushes the vulnerability information to each customer every single night. The provided information for a vulnerability can be viewed from within Nanitor by clicking on the details of that specific vulnerability.
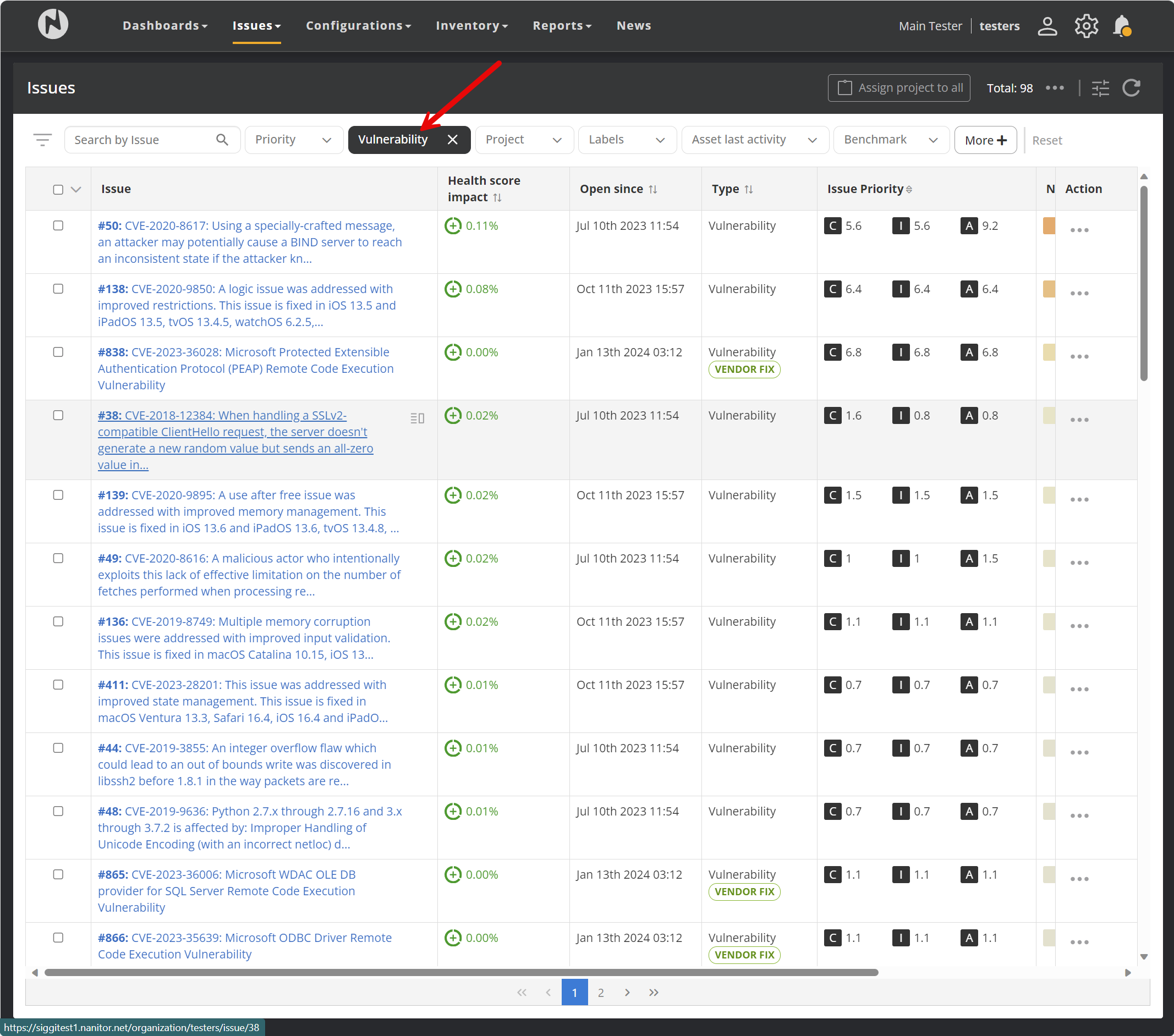
A vulnerability is treated as a specific type of issue in Nanitor. To view all detected vulnerabilities, select "Vulnerabilities" from the Issue Type drop-down menu.
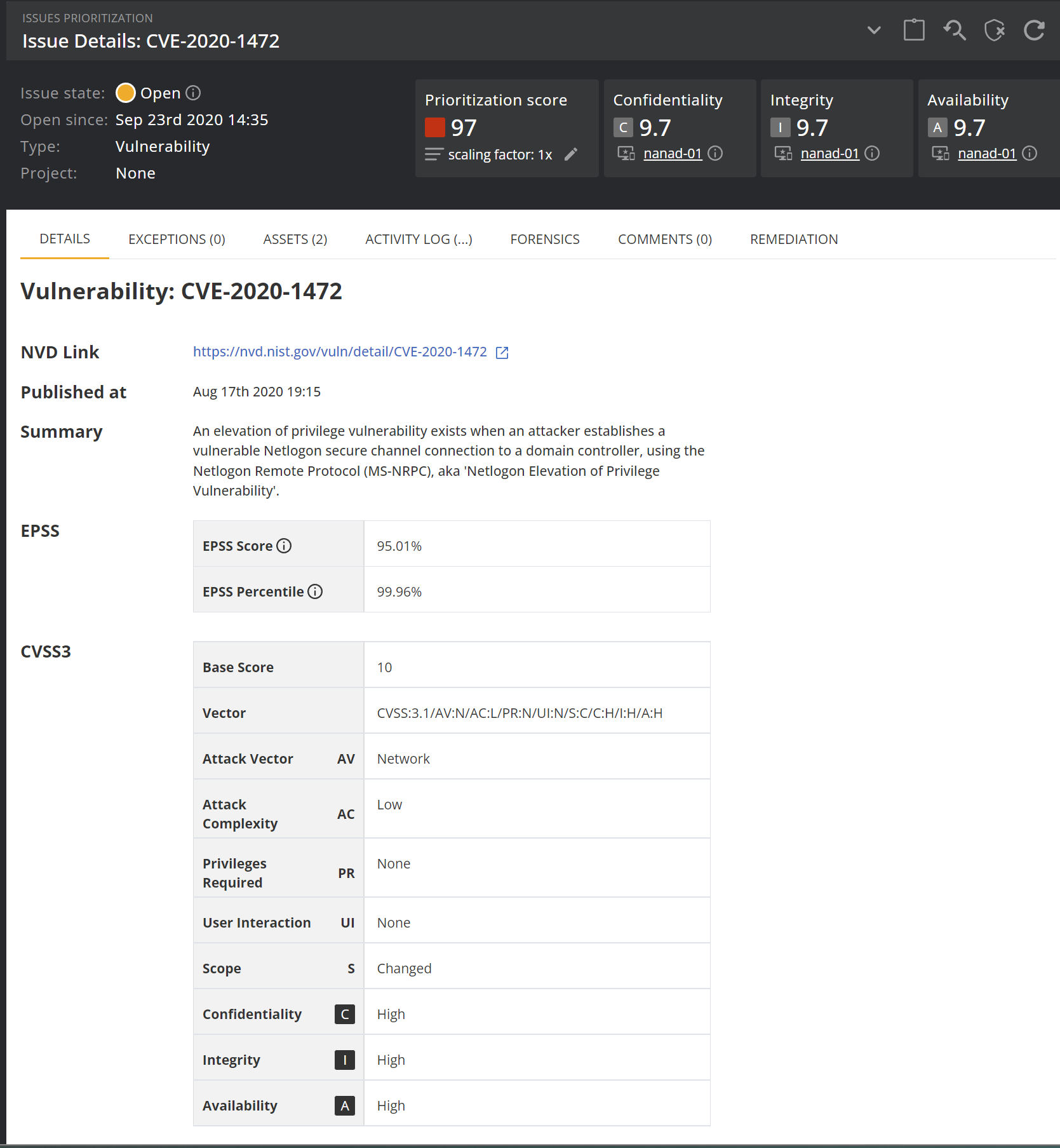
Opening a vulnerability reveals some details on the detected vulnerability such as a link to the National vulnerability database and the results of the CVSS score. The CVSS score is divided into multiple relevant vectors. The base score determines the overall severity (score between 0 and 10). Nanitor is matching the CVSS score to the three vectors of an issue (confidentiality, integrity and availability).
From the different tabs on the vulnerability detail page, you can get more detailed information on which assets this vulnerability has been detected on (assets), on which assets or labels the vulnerability has been excluded for non-applicable reasons (exceptions) and the activity log gives you more details on when a vulnerability has been detected or being removed from specific devices.
Forensics
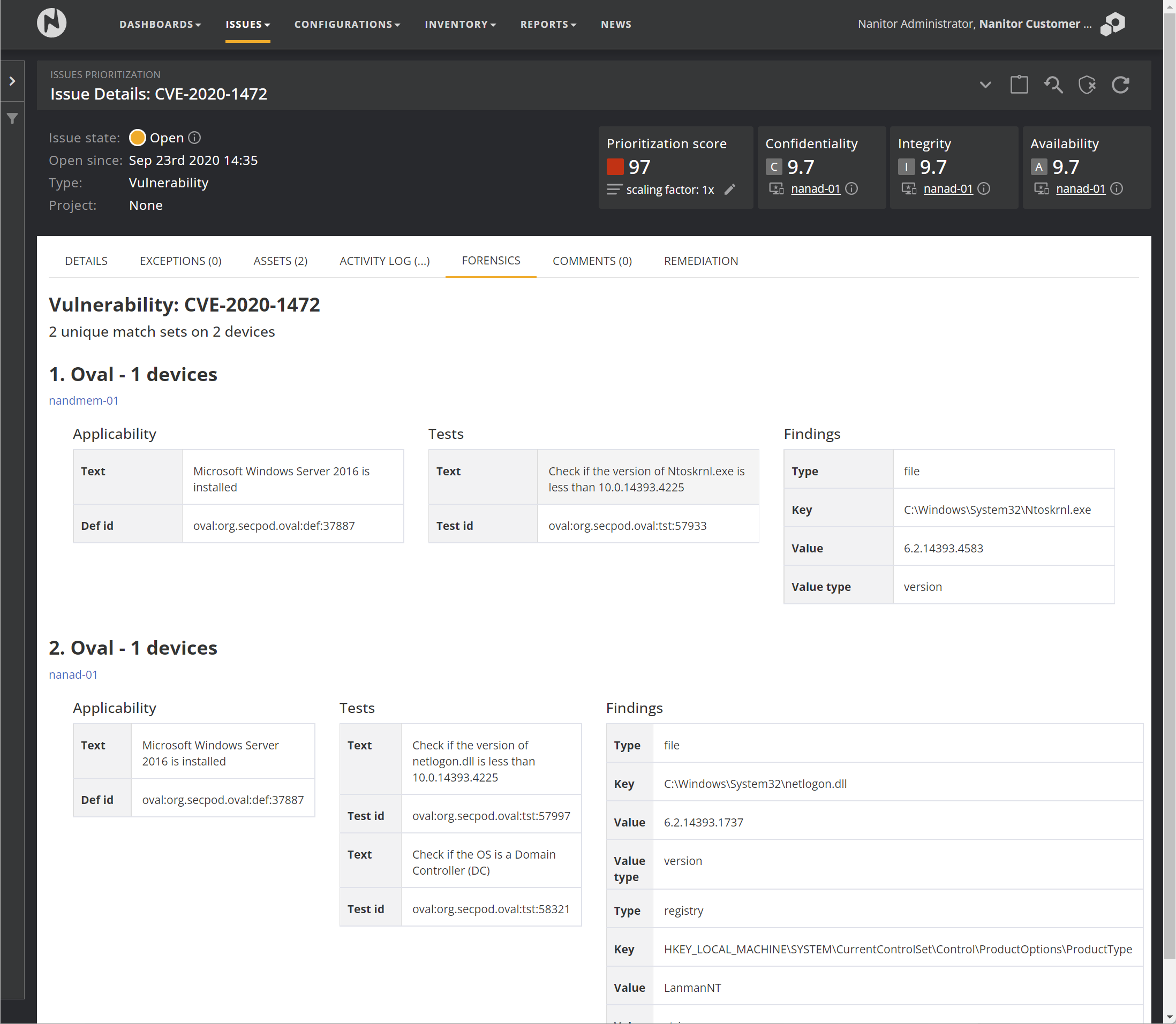
One of the most valuable features in Nanitor for the the vulnerability detection is the ability to see where or how the vulnerability has been detected on each single device. These details can be viewed in the Forensics tab of the vulnerability. The forensic section will group the same findings on the assets together so you can exactly see where to look for the vulnerability on the asset where the vulnerability has been detected on. The text description gives additional information what and which check exactly has been performed to discover the vulnerability.
The forensics information helps in the evaluation process to decide if a vulnerability might be not applicable and there should be excluded from the discovery from Nanitor
The vulnerability database
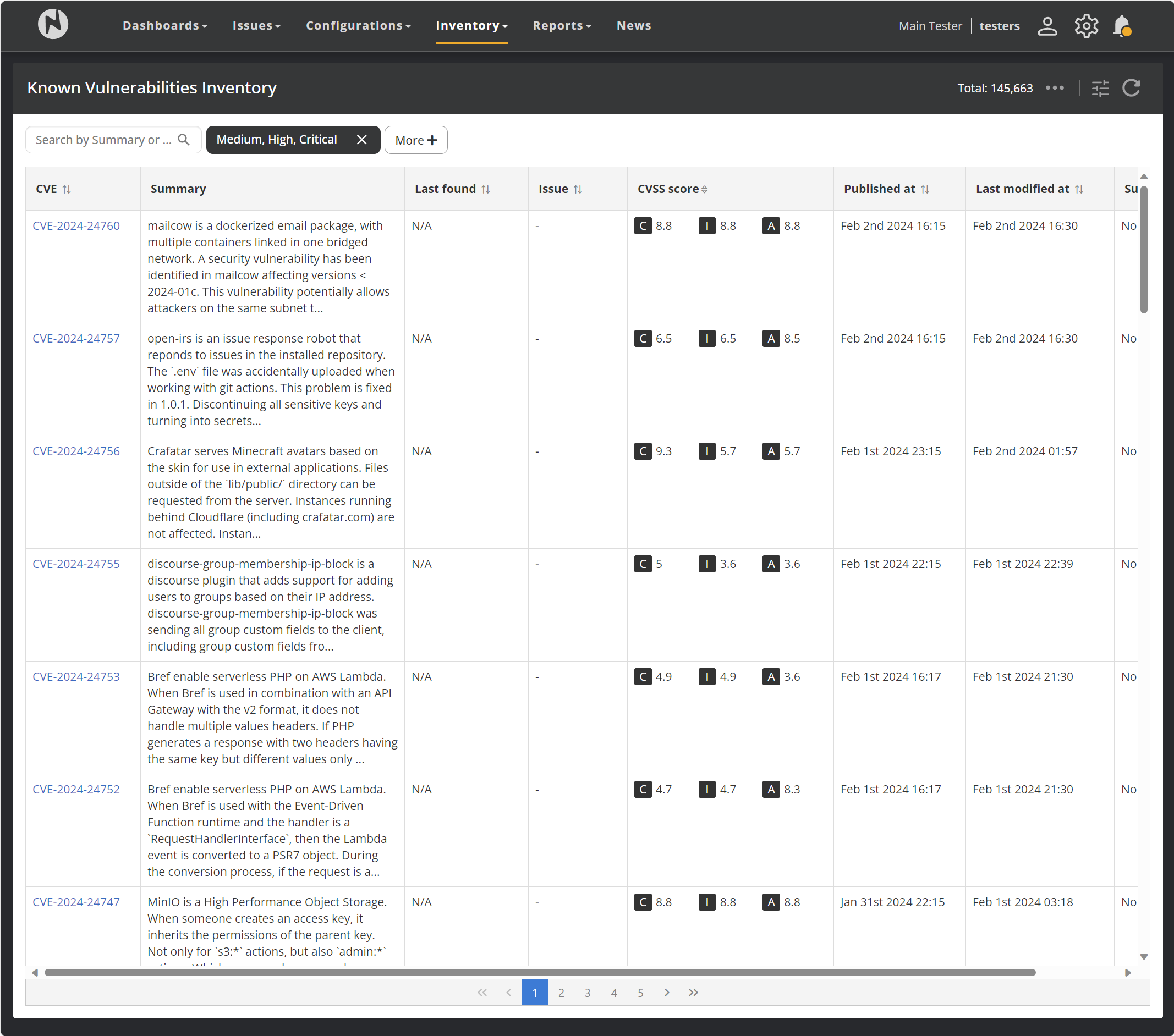
There might be the case that you need to check on a non-detected vulnerability by Nanitor (it does not appear in the issue list). Nanitor stores all vulnerabilities from its feed in your Nanitor instance for you to look it up. Some vulnerabilities might be published but not having enough information for Nanitor to fully quantify the issue. Navigate to "Known vulnerabilities" from the "Inventory" menu presents you a complete list of all vulnerabilities in Nanitor.
From here you search for a specific vulnerability that you are interested in by entering for example the CVE number in the search filter on the top left or on the severity range. The vulnerability database will also tell you when a vulnerability has been detected for the last time on an asset and what is the exact status of it. The CVSS score might not be populated for newly discovered vulnerabilities since that information is usually fed later from NIST after its initial discovery (pending analysis).