Release notes

- Version: 4.9.0
- Build number: 12218
- Release date: 2024-03-18 (general availability)
- Benchmarks release date: 2024-03-20
- Server version: nanitor-4.9.0.12218-14578-master
- Agent version: nanitor-4.9.0.12214-14577-master
- Collector version: nanitor-4.9.0.12214-14577-master
Welcome to Nanitor v4.9.0! In this version, we are introducing landmark features and enhancements aimed at MSSPs, identity security, external asset management, and asset archival flexibility.
These updates help strengthen Nanitor's position as a leader in Continuous Threat Exposure Management (CTEM), offering our users unparalleled visibility and control over their cybersecurity landscape.
Highlights
MSP Dashboard: Global Overview for MSSPs
We are proud to introduce a comprehensive dashboard for MSPs and MSSPs, enabling a global overview of customer organizations in a single pane of glass. This feature is designed to empower MSSPs with efficient navigation and management across multiple organizations, enhancing their ability to monitor and respond to threats quickly.
Key Benefits:
- Unified dashboard for an at-a-glance view of all customer organizations.
- Direct navigation to critical areas such as top issues and assets at risk.
- Strengthened MSP/MSSP customer segment, offering expanded opportunities for growth and collaboration.
The Global Dashboard, shown in the screenshot below, gives an overview across all organizations in the system.
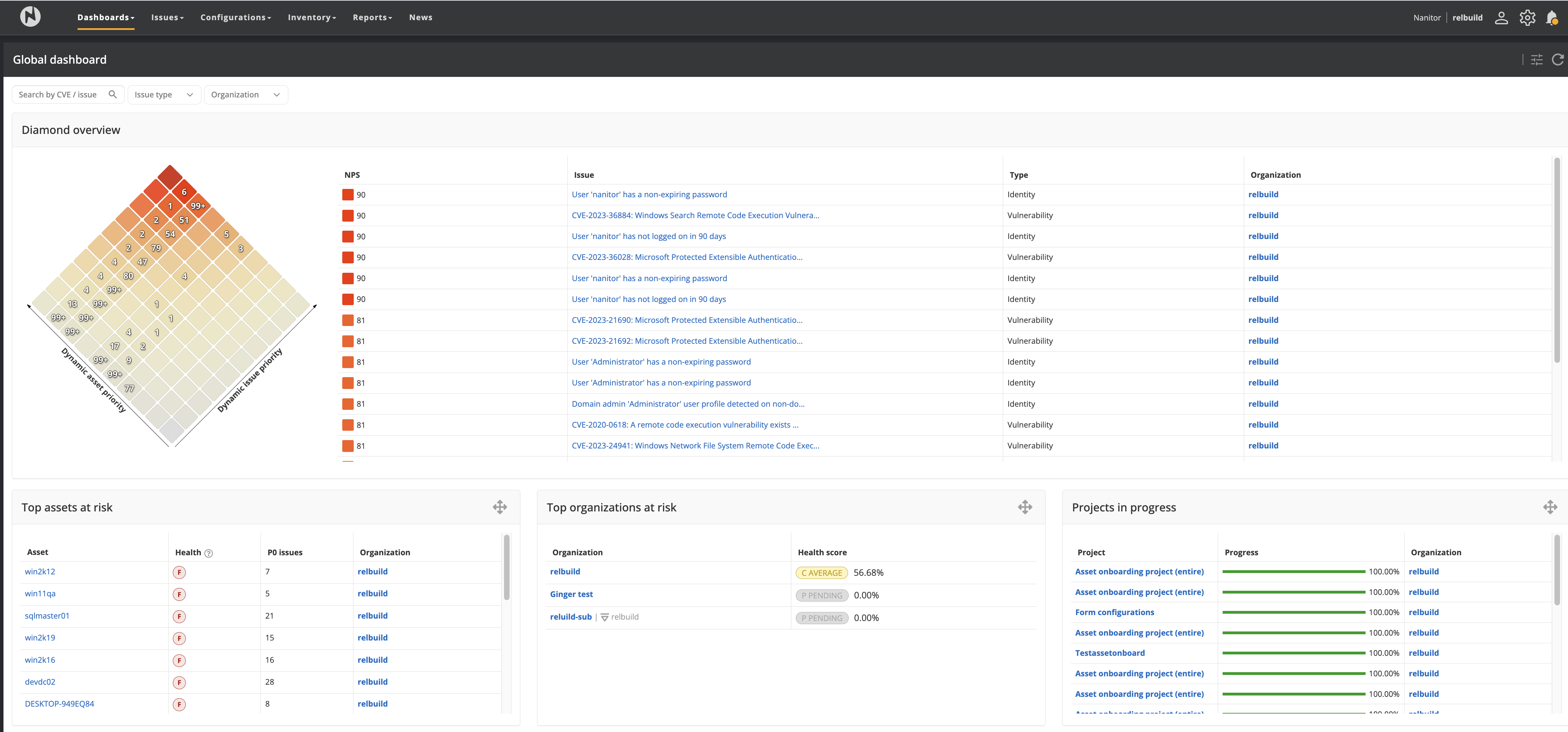
The Global Dashboard contains 7 new widgets:
-
Diamond overview: shows and lists issues across all organizations, listing the affected organizations.
-
Top assets at risk: shows the assets with the worst security posture, which potentially require attention.
-
Top organizations at risk: shows the organizations with the lowest health score, which potentially require attention.
-
Issue overview: shows an overview of the issue distribution in the organizations into P0, P1, and P2 priority groups.
-
General overview: shows the list of organizations, asset distribution, health score, and P0 issue count.
-
Projects in progress: gives an overview of ongoing projects across the organizations.
-
Asset search: provides a quick way to search across all assets in all organizations.
Identity Security Enhancements: Automated AD Identity Discovery
Our continuous commitment to enhancing identity security has led to the introduction of new issues and significant UI/UX improvements. These updates aim to streamline the management and security of identities across your environment, ensuring robust protection against identity-related threats.
In the background, we also have been improving the performance for fetching the AD identity data from the DC, as well as refactoring and cleaning up our previous logged-in user tracking that forms the backbone of our identity security support.
The most notable new feature is that AD Identity Discovery is now automated as long as it is enabled under Organization Settings - Asset discovery - Active directory discovery.
New Features:
- Detection of "KRBTGT user has an old password" issue, highlighting potential vulnerabilities in your identity security posture.
- Renovated Identity Inventory UI, offering an intuitive and efficient user experience.
- Automated AD user discovery mechanism, simplifying the process of identifying and managing user identities.
NOTE: The information can be refreshed upon request with the Run discovery now button.
EASM: External Asset Vulnerability Flagging
With the latest enhancements in External Asset Security Management (EASM), users can now gain comprehensive insights into vulnerabilities affecting their external assets. This phase brings multiple fixes and improvements, providing a clearer picture of your external threat landscape.
Key Outcomes:
- Improved visibility into external vulnerabilities, enabling proactive threat management.
- Streamlined overview of external assets, facilitating effective risk assessment and prioritization.
The screenshot below shows an example of external vulnerabilities reported on an external asset:
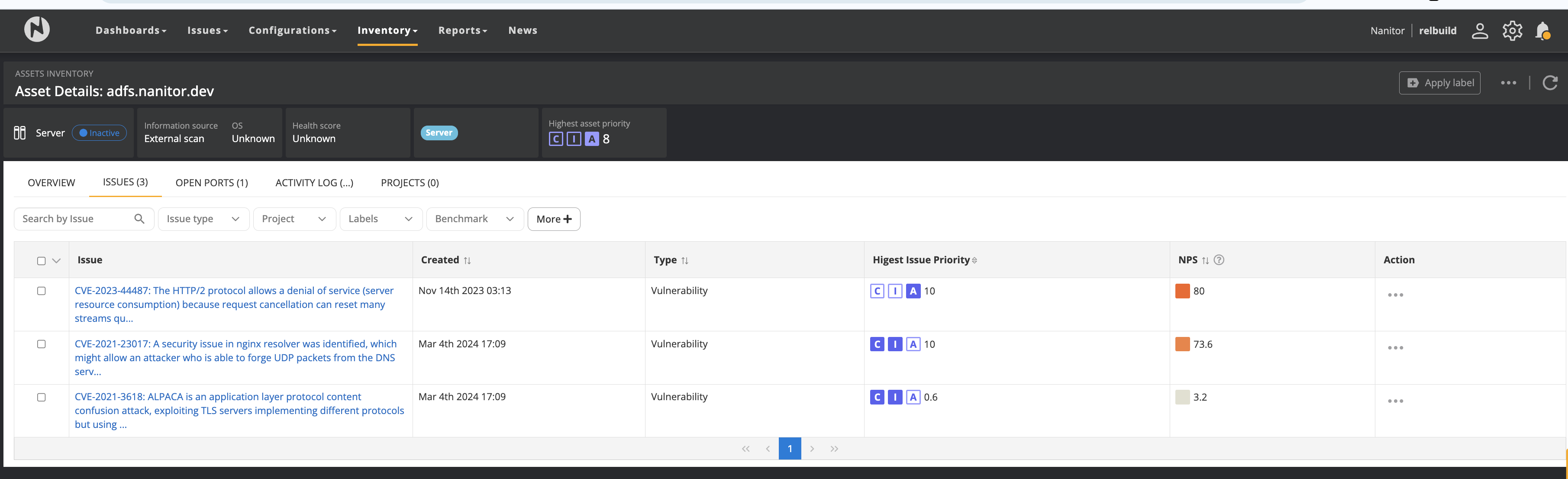
NOTE: Our EASM reporting is based on data from shodan.io that scans the internet (full IPV4 set of IPs) once per week. Thus, it may take up to a week for vulnerabilities to disappear once they have been updated. We are considering adding a way to refresh the information more quickly. Please get in touch with us if that is of interest to you!
Asset Archival Rules: Enhanced Flexibility
To address the challenges associated with managing short-lived assets (such as in cloud autoscaling groups, etc.), we've introduced the capability to define archival rules based on asset labels. This feature provides the flexibility needed to manage the lifecycle of dynamically changing assets efficiently.
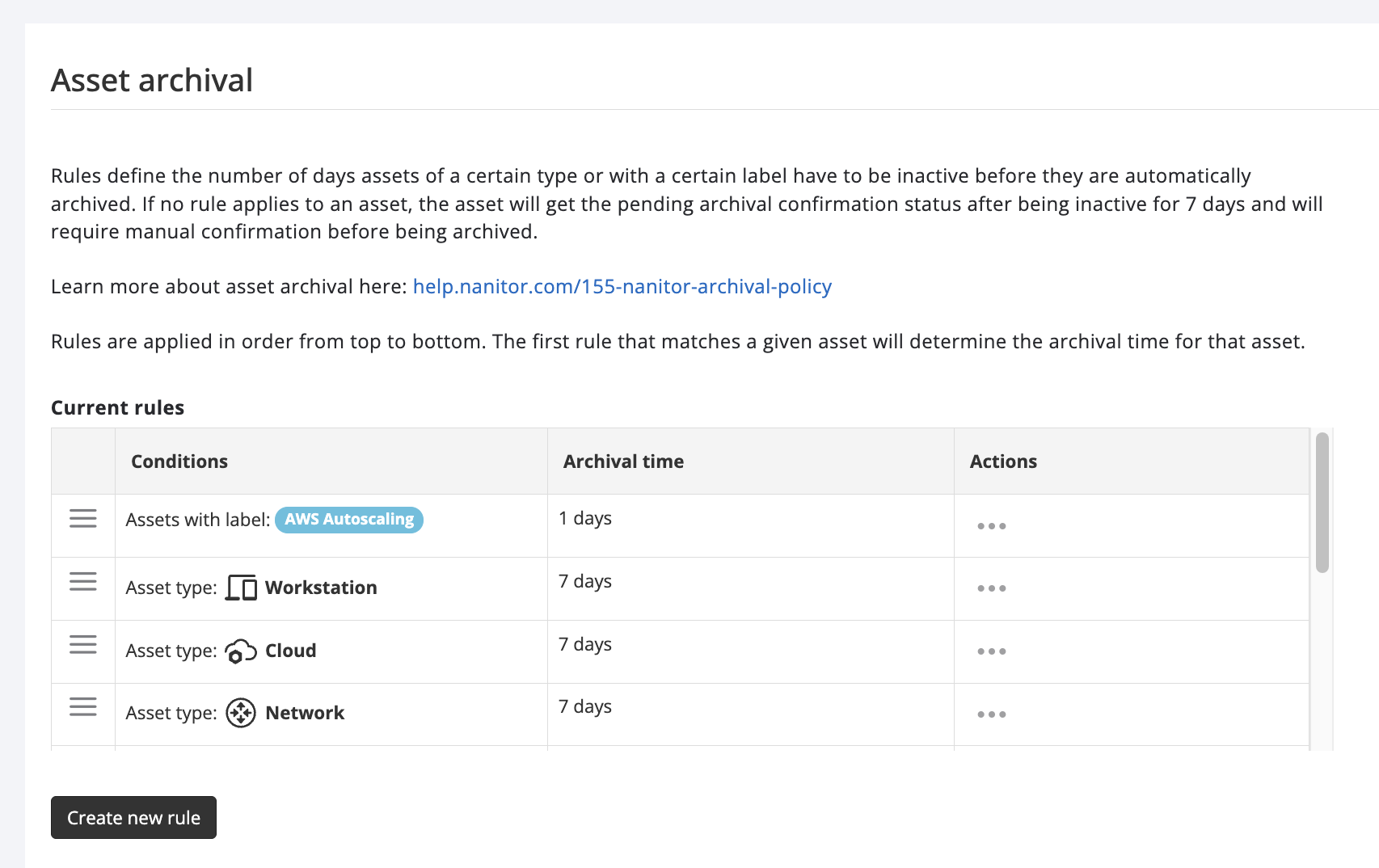
Benefits:
- Customizable archival rules tailored to specific asset characteristics.
- Improved management of short-lived servers and containers, ensuring relevant data retention and compliance.
Benchmark updates
In this release, we're strongly improving support for Fortinet with an implementation of the CIS Fortigate benchmark with a large number of automated checks. This is very valuable for customers that are using the Fortinet ecosystem for their networks.
Our upcoming benchmarks, set to release shortly after the product launch (see more details in the release information header on top), will automatically integrate with the Nanitor server without requiring any manual actions from our customers.
New benchmarks
- Fortigate (revision 1): based on CIS benchmark version 1.2.0 (CIS Fortigate 7.0.x Benchmark). Automated checks are included for 28 rules, with 25 additional manual rules. The rules have also been classified with critical / high / medium / low severities, and assigned to the default baseline based on our classification system. The benchmark can be set up through the Nanitor Collector.
NOTE: Our previous minimal Fortigate benchmark has been deprecated in favor of this much more comprehensive benchmark.
- AlmaLinux 9 (revision 1): based on CIS benchmark version 1.0.0 (Alma Linux 9 Benchmark). Automated checks are included for 232 rules. The rules have also been classified with critical / high / medium / low severities, and assigned to the default baseline based on our classification system. The benchmark will be assigned automatically when the Nanitor Agent is installed on the system.
Updated benchmarks
-
Apache HTTP Server 2 (revision 9): based on CIS benchmark version 2.0.0 (Apache HTTP Server 2.4 Benchmark). Rule checks were improved to address false positives.
-
9.2 Ensure KeepAlive is Enabled
- 9.4 Ensure KeepAliveTimeout is Set to a Value of 15 or Less
- 9.3 Ensure MaxKeepAliveRequests is Set to a Value of 100 or Greater
Improvements
-
Linux agent improvements
- Agent has been improved to run smoothly on SELinux-based systems like RedHat 9.
- New yum repository for RedHat packages with signed packages available for the agent. More information: https://help.nanitor.com/LinuxAgentRepositories/
-
Benchmark details have been improved so that "All rules" can be selected. This helps when for example editing the Baseline settings for a benchmark.
-
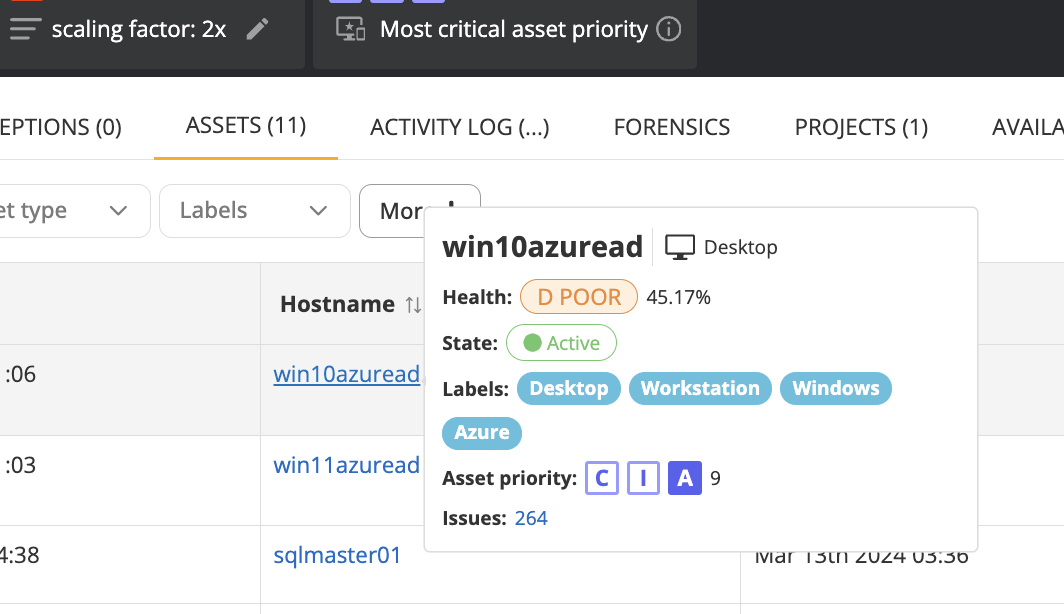
Assets now have an on-hover summary for quickly getting information. This is intuitive and helps get quickly getting context without clicking and losing context.
- Speed time to initial results. The time for getting benchmark results after installing an agent on an asset has been improved significantly. Our goal is to keep this swift and avoid wait time, especially during onboarding.
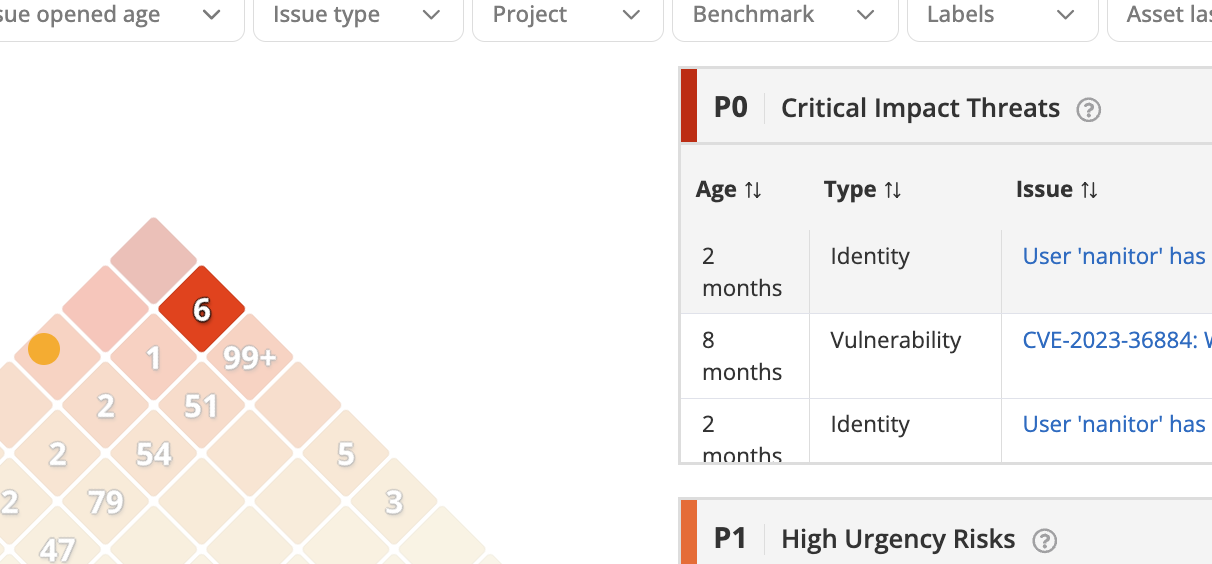
- The Diamond issue prioritization has been updated to highlight where an issue lies on the Diamond when the issue is hovered, for more intuitive UI/UX:
- The digest email has been improved to look better on Android phones with a black background.
- Collector history has been further improved to ensure we capture all connections made to collected assets for full transparency.
- Added 'CISA listed vulnerabilities' filter and new column to "Known vulnerabilities" page.
- Some fixes regarding the "Project progress" widget in the Overview dashboard and making it consistent with recently updated Project statuses.
Bug fixes
- EASM improvement filtering out discovered assets where the hostname does not fully match the specified domain.
- Fixed problem in AD Identity discovery where there was an error when there were over 5000 identities. Performance for capturing the information was also significantly improved.
- A bug was fixed in the Identity inventory where the UI would time out in some cases.
Documentation Updates
- Organization Management User guide documentation with more details on how organization management works.
- Global dashboard User guide documentation added to the Reports and dashboard documentation.
- Linux Agent Repositories KB help article added regarding Linux repositories.
Updates
- 2024-03-13: Initial v4.9.0 release was published and released to early-access (EA) users.
- 2024-03-15: Fix for EA users was pushed out and confirmed to fix a problem with nanitor-manager process.
- 2024-03-18: Release published for general availability.
- 2024-03-20: Benchmarks released for v4.9.0 version.
- 2024-03-20: A new server-only build (nanitor-4.9.0.12218-14578-master) was published to limit the frequency of sending vulnerability oval device requests to the same device (once per 20 hours) to address a problem that was affecting a limited scope of servers.