Setup and configure users for the collector
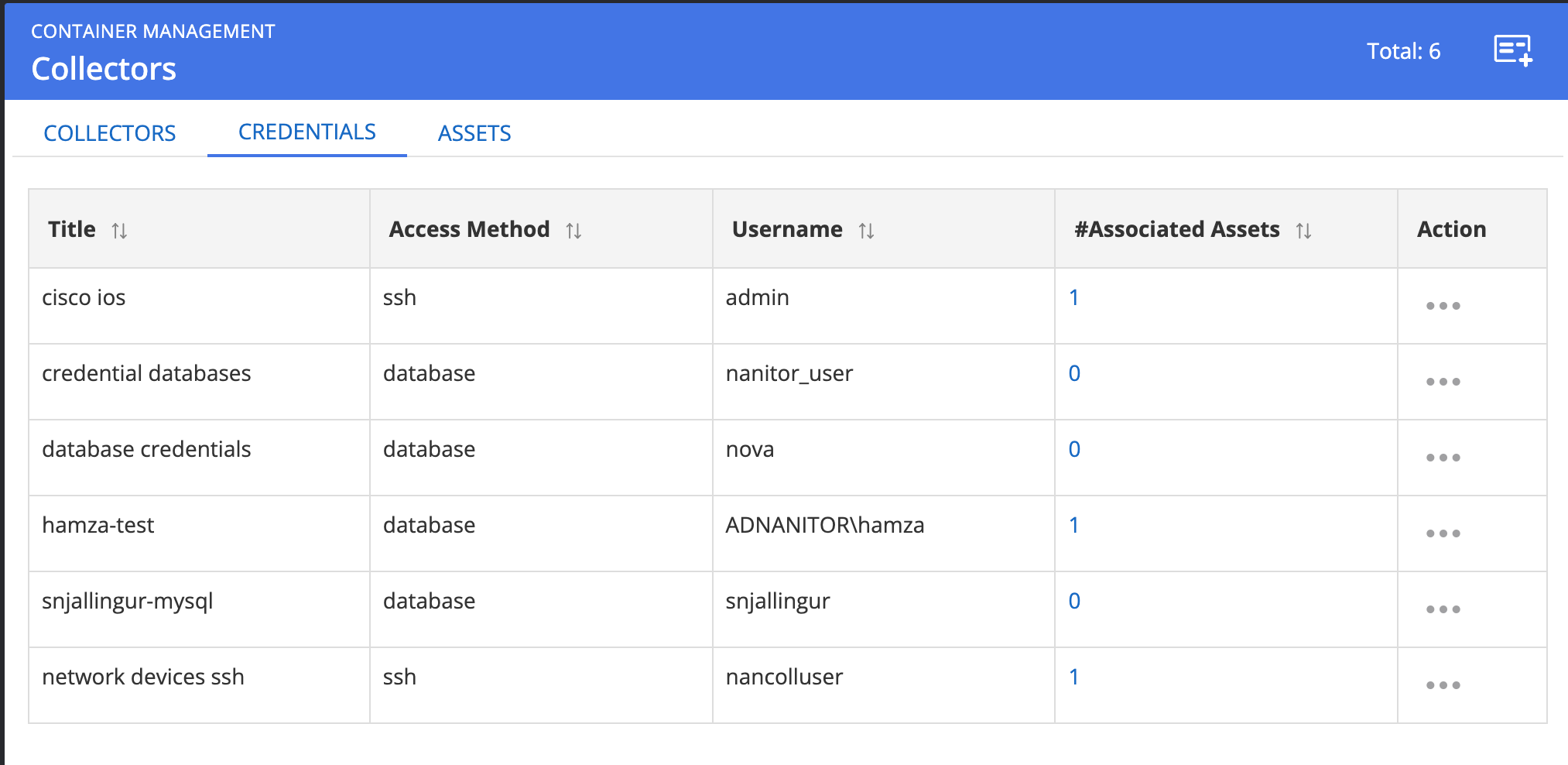
The Nanitor collector uses a user credential to log into a device (network device, database, AIX Server, etc.) to collect information from. This user is identified with a username and a password and is referred to as credentials in Nanitor. The collector operates by connecting to a specified device, log-in with specified credentials, and collecting information about the device. It is important that the credentials provided have admin privileges as much of the information that needs to be collected is only viewable by admin-type accounts. The collector will only issue commands that show information, at no point does the collector issue any commands that make any changes to anything. For Cisco-type devices, for example, this means the collector needs to be able to enter enable mode and issue privilege show commands, some of which require level 15 privilege. At no point does the collector enter configuration mode nor use any command other than show commands. Here is what the credential screen looks like
A credential has a name (title), an access method, a username, and a password, Depending on the access method there could be optional/additional information that can/needs to be provided.
Users privileges for various platforms
The users for the device need to have specific permissions depending on the platform/device from where the information has been collected from
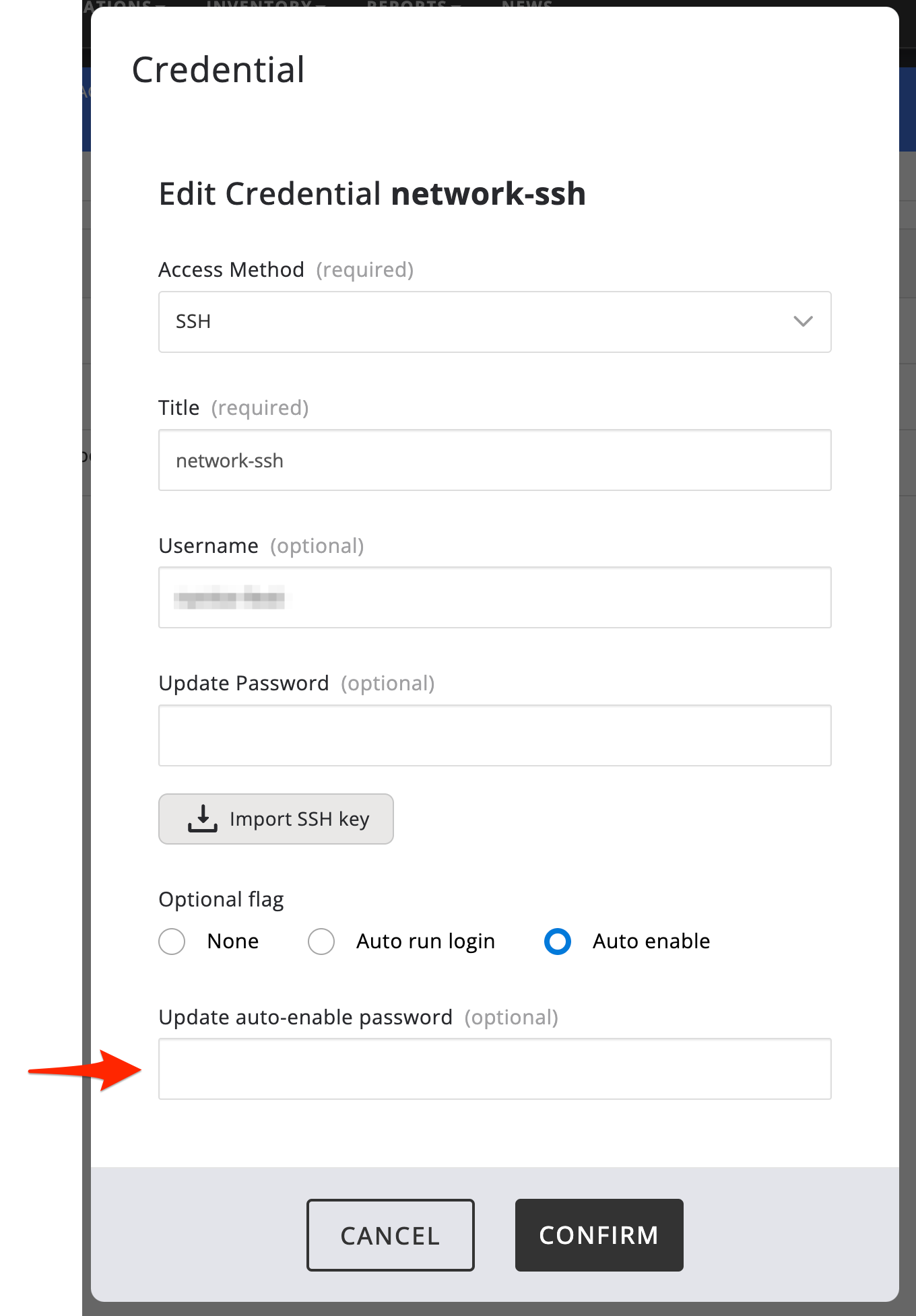
General SSH or Telnet user
Some devices require that you either enter some sort of an enable mode or switch to a super user before you can issue privileged view commands. These sorts of privilege escalation tend to come with their own password. If the device you are configuring a credential for has this sort of requirement, make sure you select the "Auto Enable" radio button and enter the required password in the appropriate field.
Oracle
- You need to have an Oracle user with the following privileges at minimum:
- CREATE SESSION
- Role SELECT_CATALOG_ROLE
- SELECT on SYS.DBA_USERS_WITH_DEFPWD
- SELECT on AUDIT_UNIFIED_POLICIES (12c only)
- SELECT on AUDIT_UNIFIED_ENABLED_POLICIES (12c only) Example of creating an Oracle SQL User for benchmarking (with minimum privileges): The following shows an example of creating a user with minimum privileges in Oracle SQL called nanitor_user with password mypass.
> create user nanitor_user identified by mypass;
> grant create session to nanitor_user;
> grant select_catalog_role to nanitor_user;
> grant select on sys.dba_users_with_defpwd to nanitor_user;
In addition on 12c and later
> grant select on AUDIT_UNIFIED_POLICIES to nanitor_user;
> grant select on AUDIT_UNIFIED_ENABLED_POLICIES to nanitor_user;
Microsoft SQL
The credentials are created as follows: "DOMAIN\user" where "user" is an Active Directory user and is allowed to access the database).
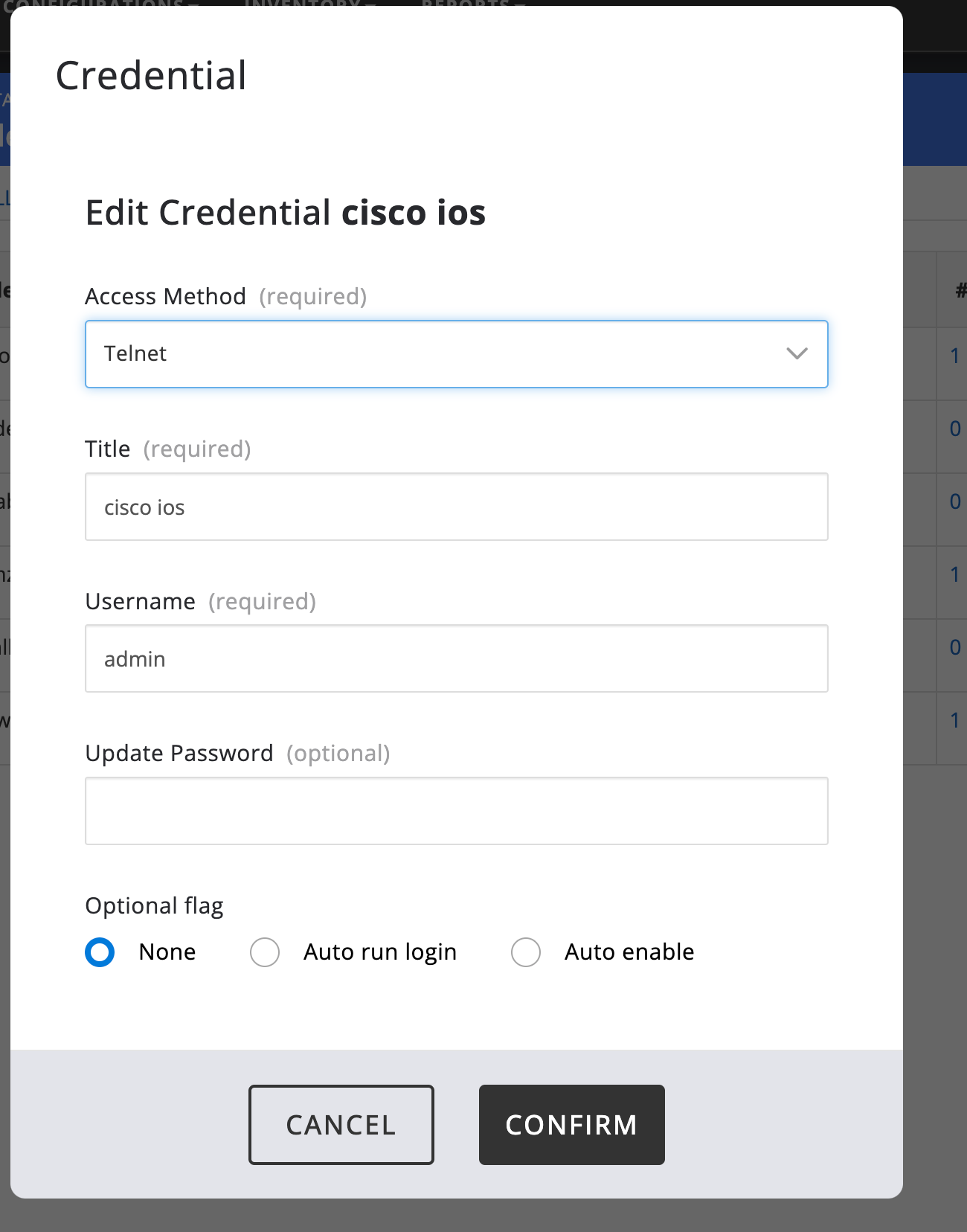
Cisco IOS
Credentials for Cisco can be SSH or telnet. A good practice is to create a seperate nanitor user and a password to use for this with privilege 15 so it can execute all the required commands on Cisco IOS. For granular authorization we recommend looking into TACACS+ to control exactly what commands this user can execute. Good practice is to only allow "show" commands, however all show commands need to be enabled so that the collector can collect all that is needed.
If the account if configured to require a separate enable password, select "Auto Enable" radio button and provide the enable password. Most cases will have None checked here.