How do I collect from Amazon EKS? (Deprecated)
This feature has been discontinued. The collector-based EKS scanning described in this article is no longer supported in Nanitor 6.8.0 and later.
For Kubernetes vulnerability scanning, see Kubernetes Inventory and Vulnerability Scanning. The new approach offers significant advantages:
- Any Kubernetes platform — Works with EKS, GKE, AKS, and self-hosted clusters, not just AWS
- No credentials shared with Nanitor — Scans run in your environment using your cluster's native credentials
- Much lower footprint — No need to download container images to a collector; scans happen in-cluster
- Better asset tracking — Deployments are tracked as persistent assets, so remediation history is preserved when you deploy patched images
- Clearer security overview — See your actual running workloads, not a cluttered list of ephemeral container images
Deprecated Instructions
The instructions below are preserved for reference only. This functionality no longer works in Nanitor 6.8.0+.
Installation (Deprecated)
Set up an Amazon user
For instructions, please refer to this article.
Install docker
For CentOS:
sudo yum install -y yum-utils
sudo yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo
sudo yum install docker-ce docker-ce-cli containerd.io
sudo systemctl start docker
sudo systemctl enable docker<br>
For Debian:
sudo apt update
sudo apt-get install ca-certificates curl gnupg lsb-release
sudo mkdir -p /etc/apt/keyrings
curl -fsSL https://download.docker.com/linux/debian/gpg | sudo gpg --dearmor -o /etc/apt/keyrings/docker.gpg
echo "deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.gpg] https://download.docker.com/linux/debian \
$(lsb_release -cs) stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
sudo apt-get update
sudo apt-get install docker-ce docker-ce-cli containerd.io docker-compose-plugin
sudo systemctl enable docker
sudo systemctl start docker<br>
Install Amazon CLI
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
unzip awscliv2.zip
sudo ./aws/install
sudo chmod -R 755 /usr/local/aws-cli<br>
Ensure AWS is in $PATH, execute the following command:
ln -s /usr/local/bin/aws /usr/bin/aws<br>
Verify by checking if the following works:
sudo -u nanitor -H aws --version<br>
Add an Amazon credential to your local environment. Place the credential in the following file:
su - nanitor
mkdir -p ~/.aws
vim ~/.aws/credentials<br>
Set up automatic Docker login. Create a file for the user nanitor-docker-login. We need to add a new line for any authenticated docker registry that should be scanned. It should look like the following. Replace the example region and user with your own information.
cat <<EOF >/usr/local/bin/nanitor-docker-login
#!/bin/bash
aws ecr get-login-password --profile nanitor-readonly-user --region us-east-1 | docker login --username AWS --password-stdin 153144908176.dkr.ecr.us-east-1.amazonaws.com
EOF<br>
Set permissions so the file can be executed:
chmod 755 /usr/local/bin/nanitor-docker-login<br>
Verify that the script works correctly by running the following. If it is successful, it will display the message 'Login Succeeded' at the end of the execution.
sudo -u nanitor -H /usr/local/bin/nanitor-docker-login
Place user Nanitor in the docker group so it can run docker commands:
usermod -G docker nanitor<br>
Adding Amazon EKS to the Nanitor Collector
Prequisite:
- You need to have your kube config ready for accessing the cluster as nanitor-readonly user.
Steps:
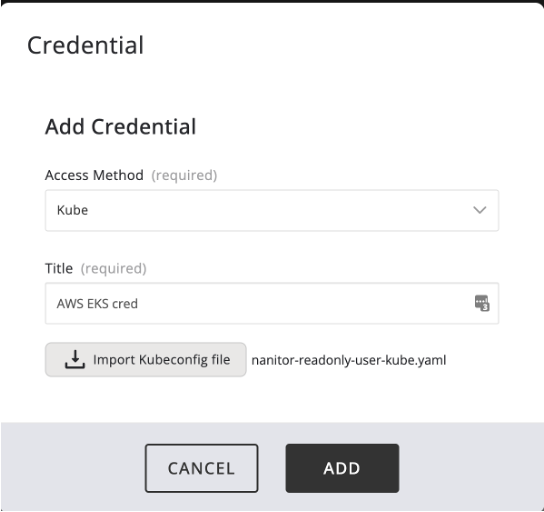
Start by creating the credential under
Admin -> Organization Management -> Collectors -> Credentials (tab)
click "Add credential" in the upper right corner.
Select the "Access Method" as "Kube" and add a fitting title.
Then you need to import your kube config yaml file.
Create an asset, and select the proper collector and credentials.
Click add, and you should be good to go.
The EKS images will be collected and scanned right away.
This step might take a while to run, if everything is successful the collector is running a vulnerability scan on the images within the Amazon container. After the cloud device has been added successfully, it should be available in the Nanitor UI.