How do I troubleshoot SSL errors on the Nanitor Agent?
The problem
The Nanitor Agent needs to trust the SSL certificate of the Nanitor Server. If it doesn't the machine won't be able to connect to the Nanitor server and it will eventually be marked as expired in the Nanitor asset inventory. Additionally, you will end up getting errors in the logs like this:
x509: certificate signed by unknown authority
net/http: TLS handshake timeout
To validate this, you need to log into the troubled machine and try to log into your Nanitor instance from that machine. When you do you should get something similar to this
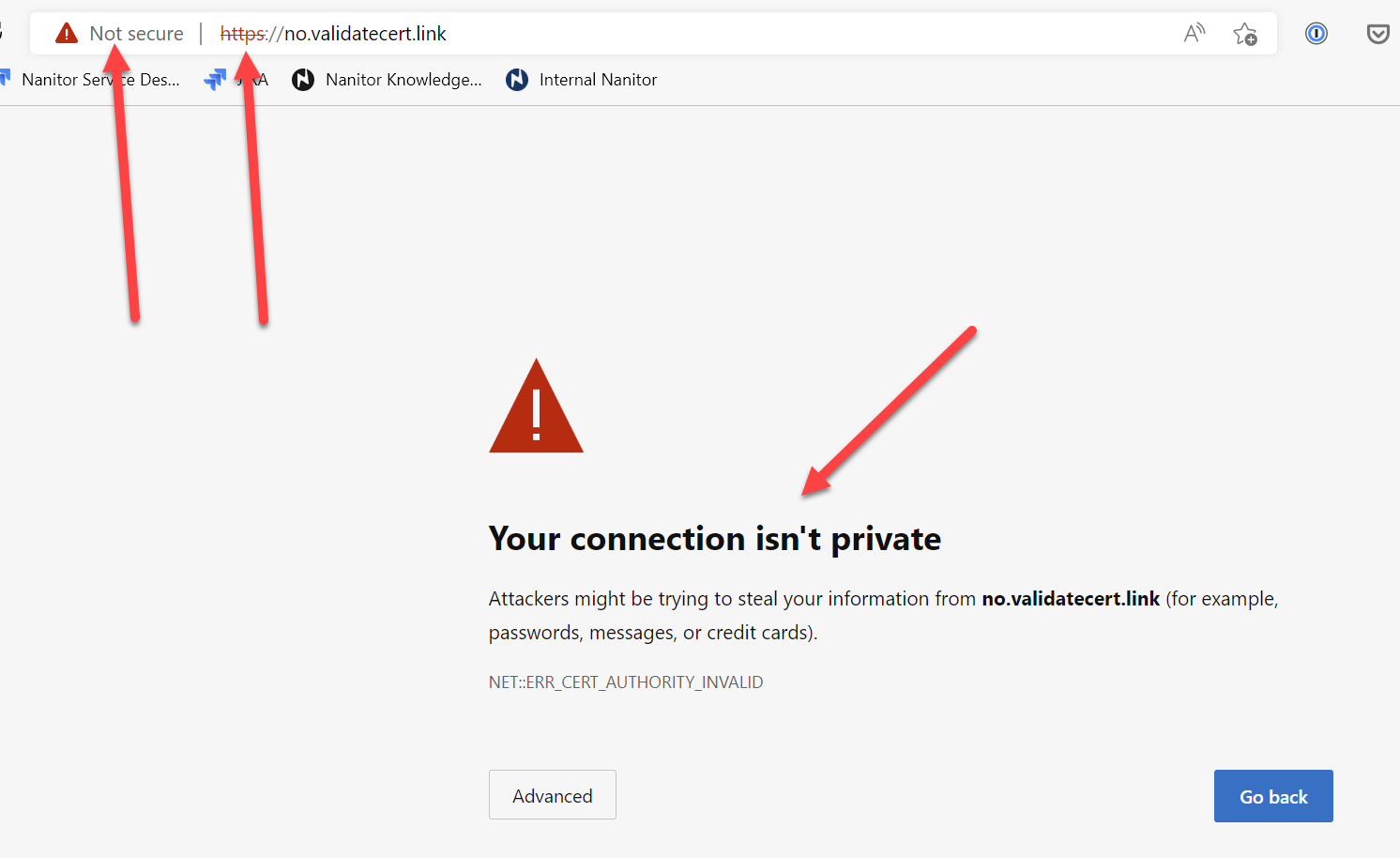 Please note I am using a known bad URL for demonstration purposes. Feel free to visit validatecert.link if you want to play with how the browser or other tools reacts to good vs untrusted certs.
Please note I am using a known bad URL for demonstration purposes. Feel free to visit validatecert.link if you want to play with how the browser or other tools reacts to good vs untrusted certs.
If you want to do this test at scale with your automation framework like Puppet, SCCM, Chef, Ansible, etc., simply use curl. Assuming a Nanitor installation at https://demo.nanitor.com (your installation will be different, that's our demo installation) you would run this command against your systems:
curl https://demo.nanitor.com
Depending on the operating system it will give slightly different error messages, but it will likely be one of these
curl: (60) SSL certificate problem: self-signed certificate
or
curl: (60) schannel: SEC_E_UNTRUSTED_ROOT (0x80090325) - The certificate chain was issued by an authority that is not trusted.
If a system doesn't have curl, you can try wget
wget https://demo.nanitor.com
The error you'll get from wget will be something like this
ERROR: The certificate of ‘demo.nanitor.com’ is not trusted.
ERROR: The certificate of ‘demo.nanitor.com’ hasn't got a known issuer.
The certificate's owner does not match hostname ‘demo.nanitor.com’
For PowerShell use Invoke-WebRequest
Invoke-WebRequest https://demo.nanitor.com
You'll get an error similar to this
Invoke-WebRequest : The underlying connection was closed: Could not establish trust relationship for the SSL/TLS secure channel.
The solution
The solution is to add the nanitor certificate to the trusted certificate store for your OS. You can find the nanitor certificate on your nanitor server at /etc/ssl/local/nanitor.crt or you can download it here
This is how we add the nanitor.crt to the trusted store:
Microsoft Windows
certutil -addstore "ROOT" "c:\temp\nanitor.crt"
Mac OS X
sudo security add-trusted-cert -d -r trustRoot -k /Library/Keychains/System.keychain /Users/myuser/nanitor.crt
Linux
The ca-certificates package needs to be installed for this to work.
RHEL/CentOS 7 and later
update-ca-trust enable
cp nanitor.crt /etc/pki/ca-trust/source/anchors/
update-ca-trust
update-ca-trust check
update-ca-trust enable
cp nanitor.crt /etc/pki/ca-trust/source/anchors/
update-ca-trust
update-ca-trust check
cp /etc/pki/tls/certs/ca-bundle.crt /etc/pki/tls/certs/ca-bundle.crt.bak
cat nanitor.crt >> /etc/pki/tls/certs/ca-bundle.crt
cp nanitor.crt /usr/local/share/ca-certificates
/usr/sbin/update-ca-certificates