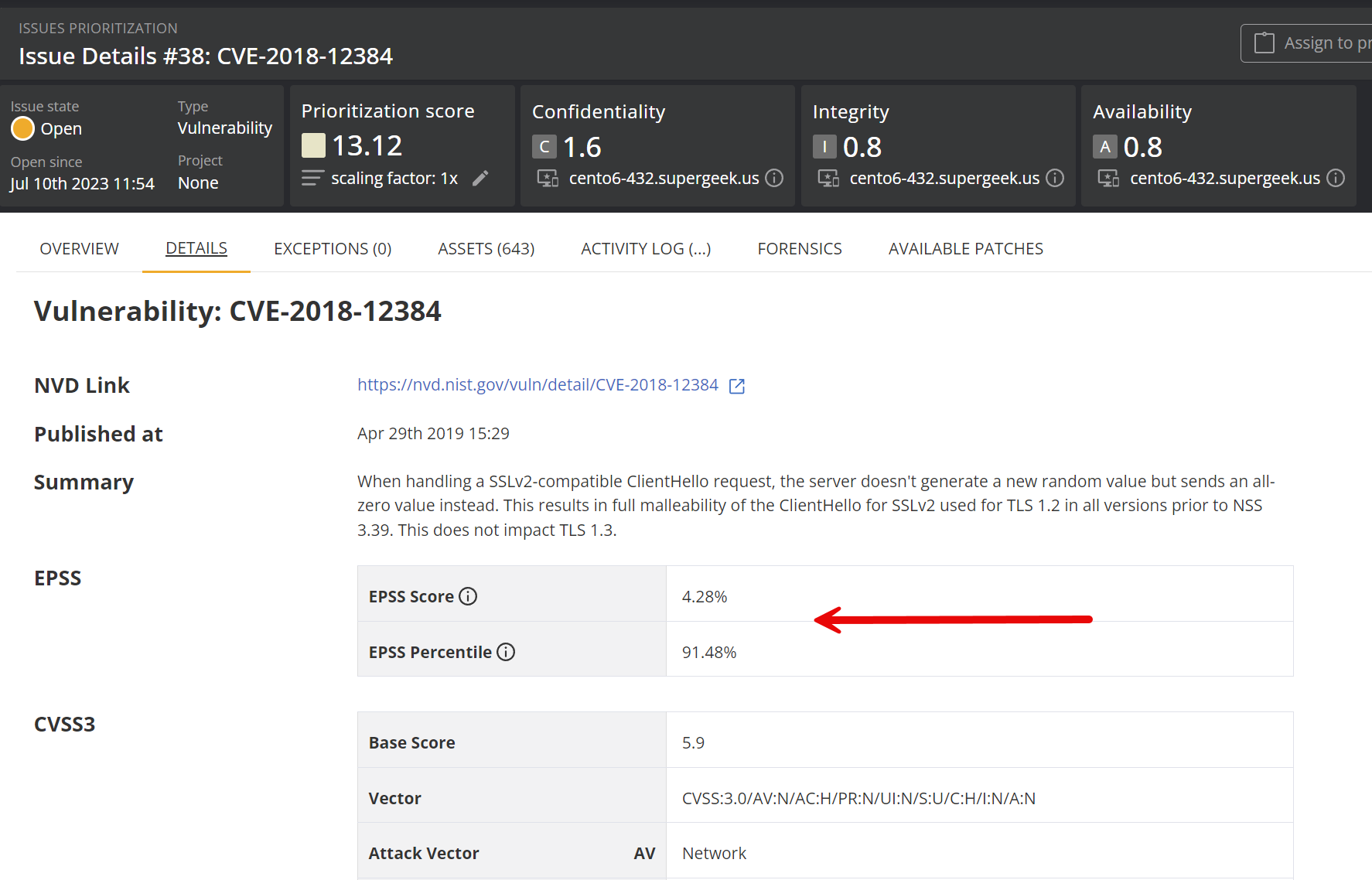
EPSS score for vulnerabilities
What is an Exploit Prediction Scoring System (EPSS)
The Exploit Prediction Scoring System (EPSS) is an open, data-driven effort for estimating the probability that a software vulnerability will be exploited in the wild. The EPSS model produces a probability score between 0 and 1 (0 and 100%). The higher the score, the greater the probability that a vulnerability will be exploited.
Until Version 2.4 Nanitor did not take the EPSS score for vulnerabilities into consideration. Since Nanitor Version 2.4. the EPSS score for vulnerabilities has been implemented and is part of the Issue priority score. Since the EPSS score can be very low for a large number of vulnerabilities it results in an immense downgrade of vulnerabilities of prioritized issues in the Nanitor diamond.
The EPSS score of a vulnerability is visible from the issue details view.
Issue priority score for vulnerabilities
All issues get their priority score by multiplying the issue priority score with the asset priority score ( refer to its documentation). For vulnerabilities, Nanitor makes an exception for the issue priority score calculation and it is computed as follows:
Issue priority score = Issue priority rating * (Issue EPSS score) 0,5 * Asset priority rating
In cases where the EPSS score for a vulnerability is not (yet) defined, Nanitor will not apply any scaling and the Issue priority score continues to be calculated as all other Issues:
Issue priority score = Issue priority rating * Asset priority rating
Effects on the Nanitor diamond
The effects on the issue ranking for vulnerabilities will lead to a massive downgrading of most of the detected vulnerabilities in the Nanitor environment. Nanitor will keep the applied calculation method under further observation and may come up with a change if the results of the prioritized issues within Nanitor do not reflect the severity of vulnerabilities it deserves.
Still, customers have the option to apply a more aggressive priority scaling factor for detected vulnerabilities to higher (or lower) the score for detected vulnerabilities ( documentation).