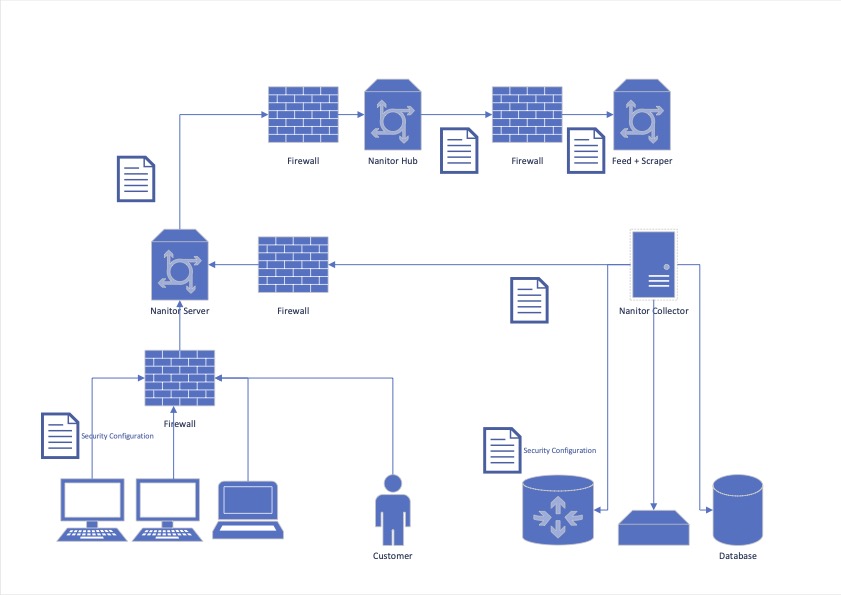
The Nanitor architecture
The Nanitor architecture is an infrastructure of several components shown in the below image. For an IT security monitoring solution, it is essential to understand how the different components work together and to know what information is pulled/pushed between them.
The main components are:
- The Nanitor Server is the key component since it receives the data from the monitored clients (assets). The Nanitor Server includes the user interface (UI) for users to configure the security level and display all captured information. The Nanitor Server is deployed on a dedicated server with a hardened Linux operating system either On-Premise or as a SaaS solution. Nanitor recommends Debian and supports any Debian derivatives (such as Ubuntu) or Red Hat Enterprise Linux and their derivatives (such as Alma). Each Nanitor customer has a dedicated instance.
- The Nanitor Collector is capturing data from connected network devices (Servers, Firewalls, Switches, and Databases). The Nanitor Collector can be installed independently on the same OS as the main server. It can also be enabled on any system running the Nanitor Agent. The Nanitor Collector is pushing all captured data to the Nanitor Server.
- The Nanitor Agent(s) capture data from all end devices (Laptops, workstations, tablets) and push all captured data to the Nanitor Server. The Nanitor agents are available for almost all Windows, Mac, and Linux operation systems.
- The Nanitor Hub is managed and operated by Nanitor and manages customer licenses and centralizes all the latest benchmark and vulnerability information to the customer Nanitor Servers. The Nanitor Servers syncs with the Hub daily and fetches the newest benchmark and vulnerability feeds.
- The Nanitor Feed keeps information keeps all information about the Nanitor benchmarks based on the benchmarks issued by CIS. The Hub continuously receives the most up-to-date and relevant benchmark and vulnerability feed information.