How to enable Active Directory (AD) domain authentication?
Active Directory (AD) authentication support allows single sign-on support in Nanitor. This automatically allows application of organizational password policy to Nanitor and typically makes it easier to remember the user credentials.
The AD authentication is established via authentication to an LDAP server and requires that the user is a member of a specified domain users group to be able to access the organization in Nanitor.
Note that users need to have their email field specified in Active Directory in order to be able to authenticate to Nanitor.
Step 1. Configure the LDAP settings
Active directory sign in/login requires updating the nanitor_common.ini file. Add a new section at the bottom of nanitor_common.ini file (typically located in /etc/nanitor):
[ldap]
server = dc-01.domain.company.com
enabled = true
basedn = "dc=domain,dc=company,dc=com"
port = 636
ssl = true
domains = DOMAIN1 DOMAIN2
The server specifies the hostname of the LDAP server (domain controller). In this case we are authenticating via SSL on port 636. The domain name (or names if more than 1) is a space-delimited list of the domain names supported. The basedn is the distinguished name for the domain.
To test that the configuration is working properly, run the command (password will be prompted):
# /usr/lib/nanitor-server/bin/nanitor-server-ctl test_ldap --domain YOURDOMAIN --username ADUsername
If successful, certain information will be outputted on the console and you can proceed.
If you get an error regarding a missing certificate, you may need to import the root certificate. See our related guide How do I troubleshoot SSL errors on the Nanitor Agent? for instructions on importing the organization root CA. Then repeat the command and verify that it works correctly.
Restart the Nanitor server once the configuration has been completed:
# /usr/lib/nanitor-server/bin/nanitor-server-ctl systemctl_restart
Note, if you sign into Nanitor at this point, make sure to select the Local option under "Domains for authentication" to authenticate with local Nanitor credentials, i.e. the email address and password.
Step 2. Assign access via AD security group.
With AD enabled, access control is via AD Security Groups. All members of a given security group can be given access to Nanitor. To create a new access group.
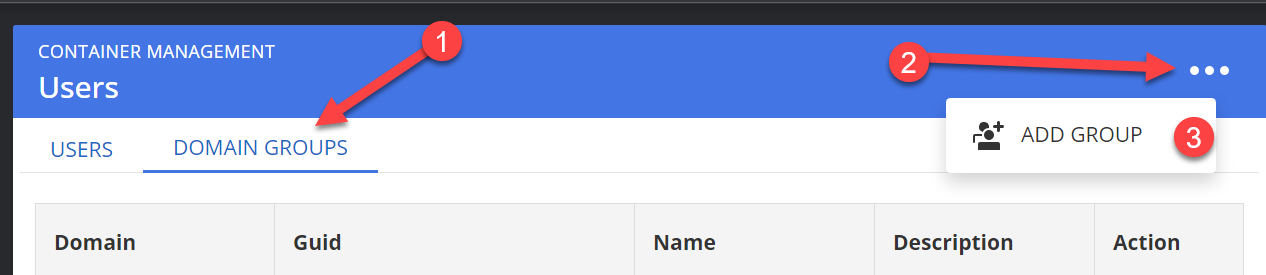
Go to Administration -> Organization Management -> Users, click on "Domain Groups", then the three dots in the upper right hand side, then "Add New Group".
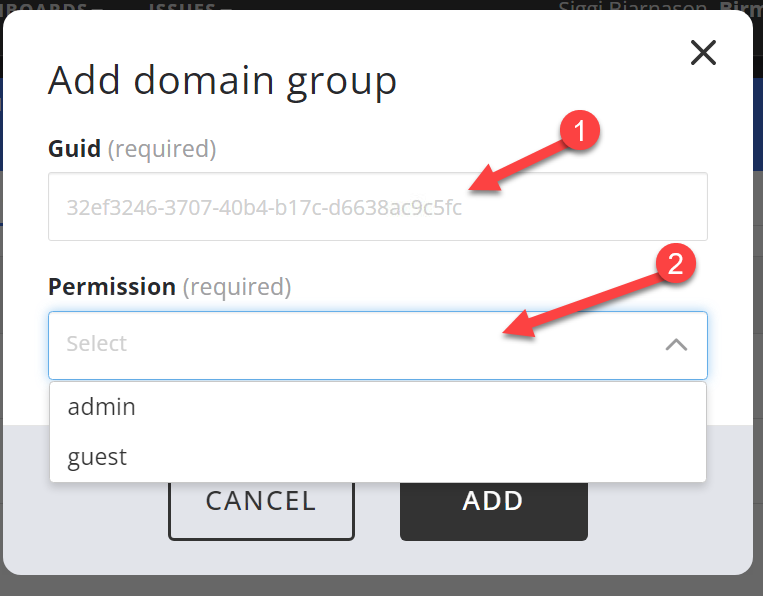
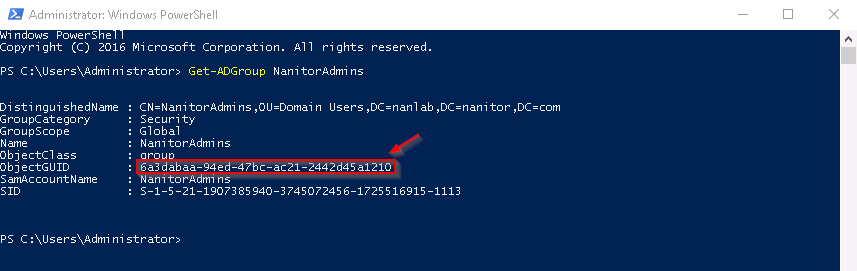
The domain group is specified by the GUID which is a unique identifier for an object in AD. To determine the GUID of an AD security group, open Windows PowerShell and run the command: Get-ADGroup GroupName and the output will be e.g.
Copy paste the GUID (ObjectGUID) into the "Domain Group GUID" field and specify the permissions as either admin or guest and click Save. The newly created group will appear in the list of domain groups. The name and descriptions fields and empty initially and are populated when a domain user logs in to the system via domain authentication.
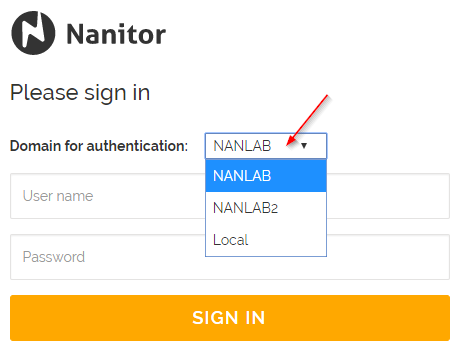
To sign in with domain credentials. With LDAP enabled, the domain selection appears on the sign-in page:
By default the first domain is selected. To log in to Nanitor with local credentials (i.e. not via AD), Local can be selected and the user can log in with email/password. When current Nanitor users log in via AD authentication (with email matching their current Nanitor credentials) their account is converted to domain authentication and previous password cleared.