How do I activate alerting and incident notifications?
Introduction
After defining your configuration baseline and initial hardening to meet the baseline (i.e. incident count to 0), you have laid out exactly how you would like your systems to be configured. If anything happens in our systems that change that assumption, we want to be notified immediately and the incident escalated to the appropriate personnel. All notifications are done via email and you send the email to your ticketing system or to one or more personnel. You can also send the alert to a slack webhook.
A typical scenario when assumptions change is when a system administrator makes changes to Group Policies and is not aware that the change might impact the security posture of the organization. Alternatively, installing software on a device might alter the configuration without the person installing being aware. Those scenarios are common in practice and can be hard to detect without a system like Nanitor.
When a particular configuration check breaks, Nanitor creates an incident, which represents the deviation from the rule. It tracks the lifespan from the first rule deviation to the last point. For example, if a Group Policy causes a particular rule to be broken on 100 devices, the first breakage triggers incident creation and the subsequent ones get appended to it. The system provides good visibility over incidents and which devices still have unresolved incidents.
An incident gets resolved when the rule is no longer deviating from the baseline set previously on any of the associated devices. Another way to resolve the incident is to remove it from the baseline. The point is that the organization can make a well-informed decision about how and when they resolve a particular incident.
The lifecycle of an incident prevents information and notification overflow as when a particular rule breaks on many devices simultaneously, only one incident gets created and only one notification sent.
The email representing the incident is thorough and describes exactly what rule has been broken and what the impact is. It includes a link to the Nanitor system, which can be clicked to get more detailed information.
Enable notifications
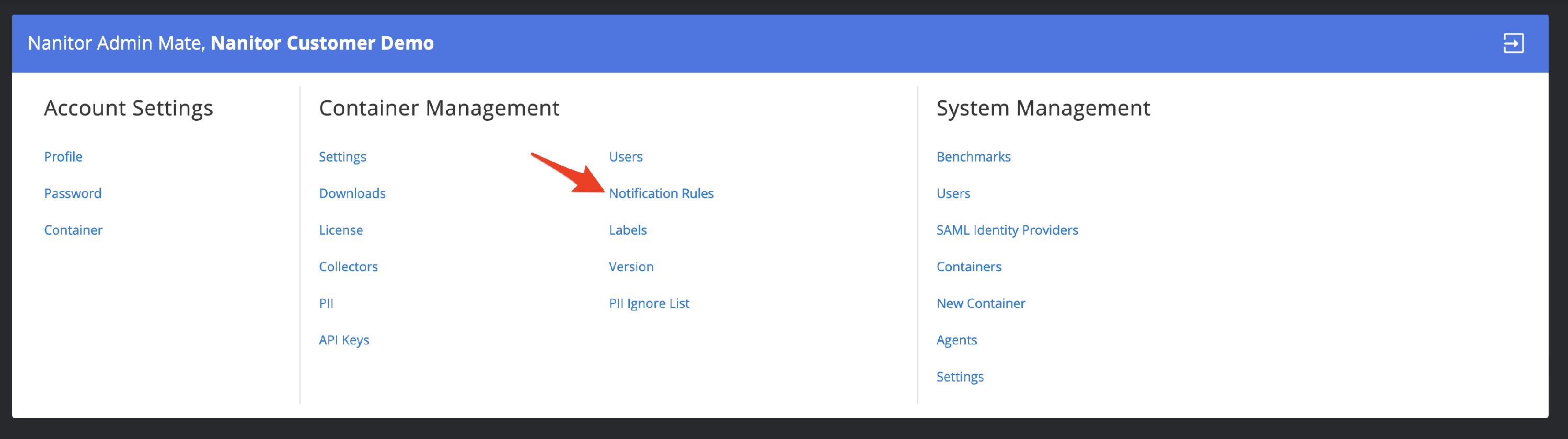
Notification can be set up for multiple scenarios. To view, edit, or create a new notification rule go to Administration -> Organization Management -> Notification Rules
This will show you a list of active notification rules in your system. Click on the button top right to create a new notification rule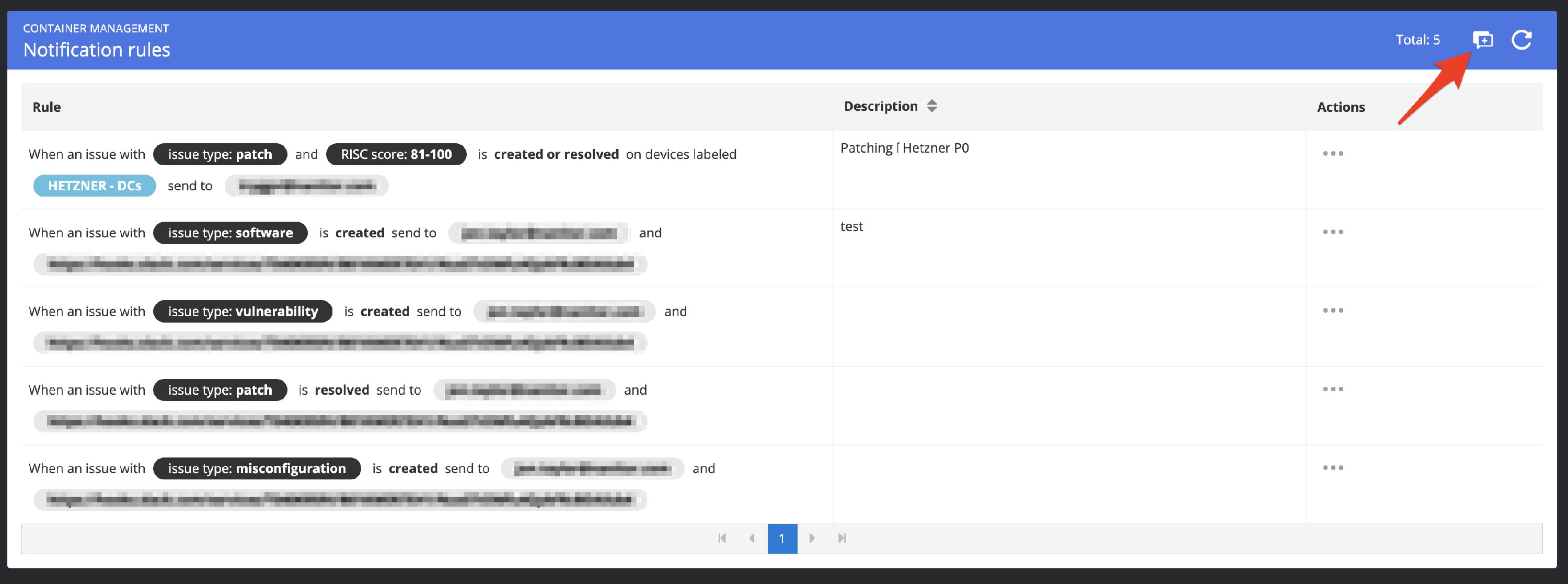
This will bring up the notification rule dialog where you can define and apply one or more rules and one or multiple email recipients.
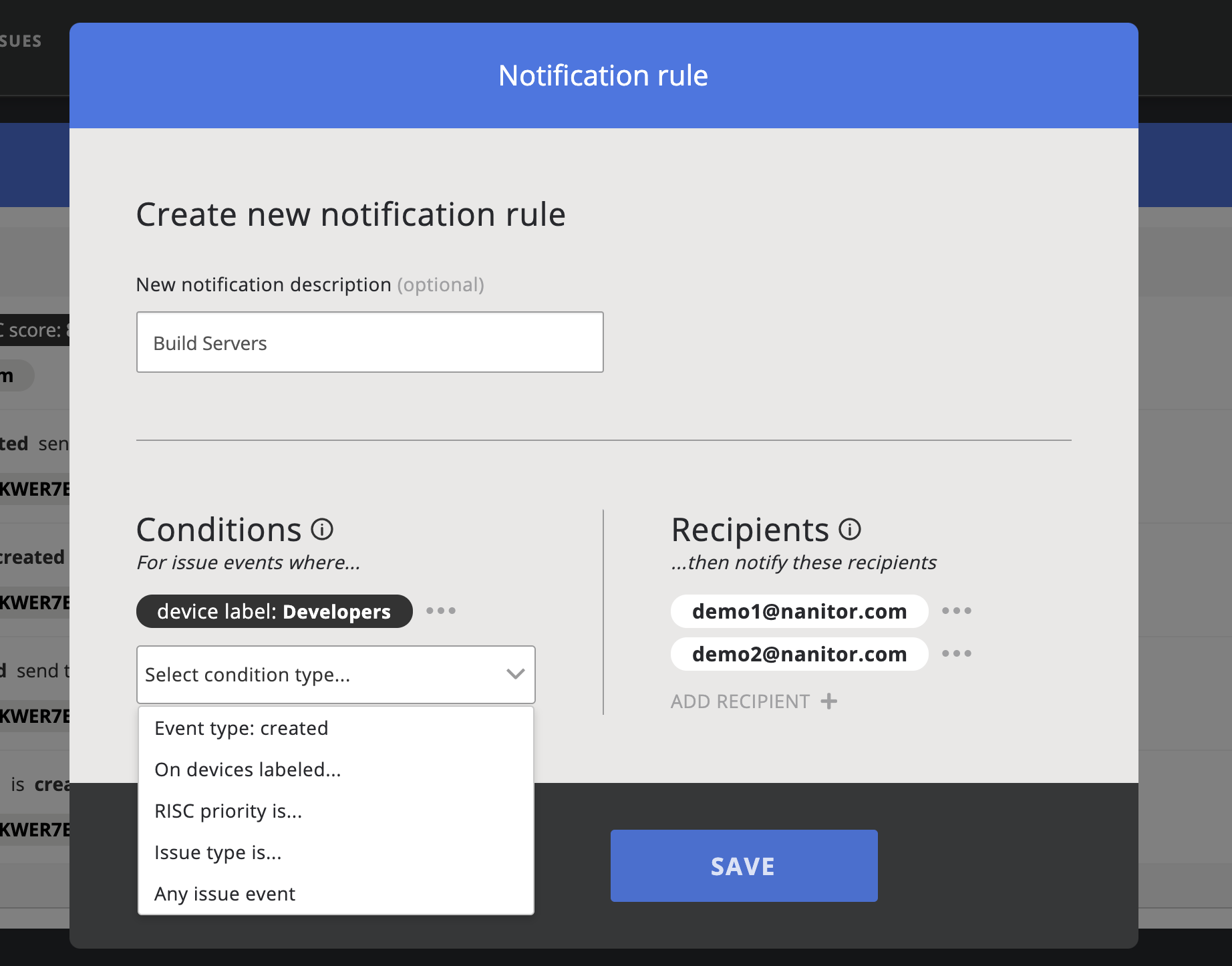 When you have a Slack app configured you can also send the notification to a Slack channel of your choice.
When you have a Slack app configured you can also send the notification to a Slack channel of your choice.
There are four types of notification types that you can select from (one or more):
- Event Types. Here you can choose between created or resolved issues. The event will be fired for any issue events
- Device Label. Select any label.
- Issue Type. Any of the issue type MIsconfiguration, Patch, Vulnerability or Software
- Any issue event
When multiple notification types are applied within the same rule they act as an AND operator. E.g. Device label "Server" and "Build DC". If you want to get a notification for either the device label "Server" or "Build DC" you will need to create two separate notification rules (one with the device label "Server" and another rule with the device label "Build DC").
For recipients, you can select one or multiple email addresses and/or one or multiple Slack channels. to send notifications to.
Click save to save and apply the rule.